Firewall Rules for MongoDB® with ScaleGrid
Easily create firewall rules for your hosting for MongoDB® to control the list of IP addresses that are allowed to connect to your database deployments. This functionality is only available for MongoDB® deployments that are open to the internet.
Only Available for Dedicated Hosting PlansIf you are using our Bring Your Own Cloud (BYOC) plan, please visit the Security Group sections of our Cloud Profile pages for AWS, OCI and Azure to see how to lock down access to your clusters. Firewall Rules are not supported in our Shared Hosting plans.
What is an IP CIDR?
CIDR is the short for Classless Inter-Domain Routing, an IP addressing scheme. A CIDR IP address looks like a normal IP address except that it ends with a slash followed by a number, called the IP network prefix. CIDR addresses reduce the size of routing tables and make more IP addresses available within organizations.
For example, we could express the idea that the IP address 192.168.0.11 is associated with the netmask 255.255.255.0 by using the CIDR notation of 192.168.0.11/24. This means that the first 24 bits of the IP address given are considered significant for the network routing.
Firewall rules in MongoDB® are added by specifying IP CIDRs. These can be added at the cluster level or account level.
Cluster Level Firewall Rules
Firewall rules can be added at the deployment level. These rules will only be applied on a per-deployment basis.
- Log in to the ScaleGrid console, and go to your MongoDB® cluster details page.
- Click on the Firewall Rules button under the Overview tab:
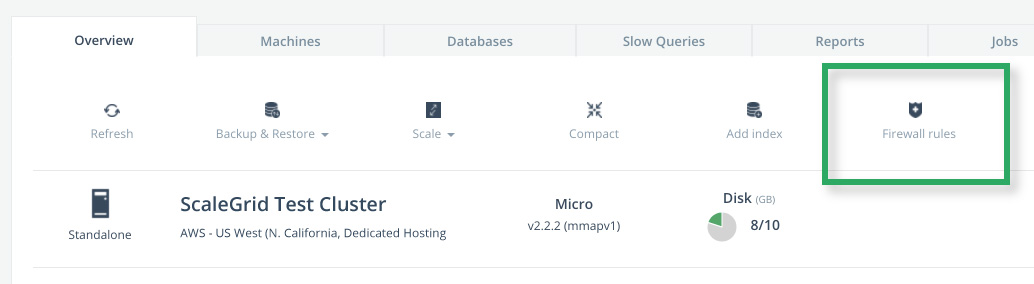
- Add Firewall Rules in the form of IP CIDRs in the open module. Only these IPs will be allowed access to the deployment.
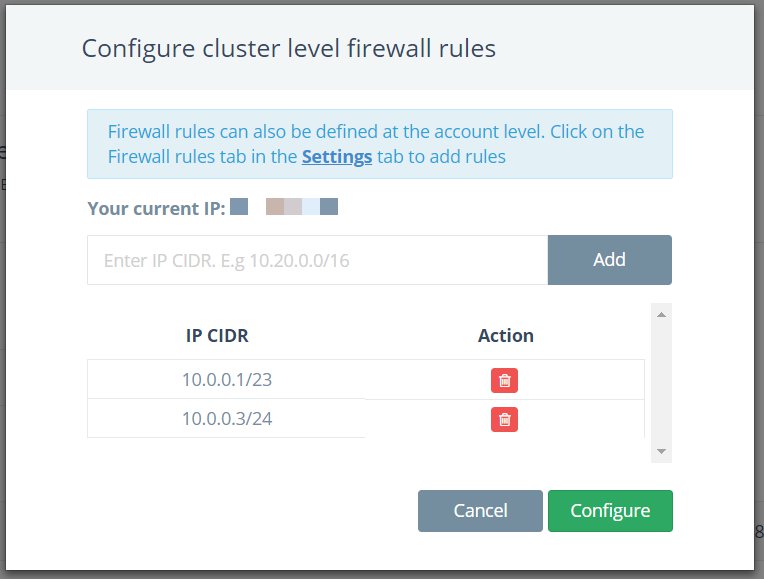
Please note that the Firewall Rules functionality is only available for deployments that are open to the internet. While using 0.0.0.0/0 to open your deployment to the internet is not recommended, you may still add it to your list of Firewall Rules.
- After you have entered the list of IP CIDRs that will be allowed access to the deployment, click on Configure. This will push the rules to the deployment and apply them
Make sure that you update all apps using this deployment to reflect the new access rules.
Account Level Firewall Rules
You can also set up Account Level Firewall Rules. These will be pushed to all deployments in your account irrespective of the database type.
The advantage of using account-level rules is that you don’t have to repeat the same firewall rules per deployment.
- Log in to the ScaleGrid console.
- Go to Settings > Global rules > Firewall rules:
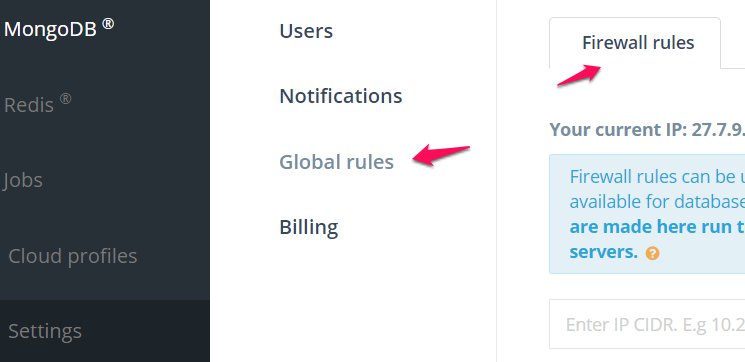
- Add your Firewall Rules in the form of IP CIDRs. These IPs will be allowed access all of your database deployments at ScaleGrid.
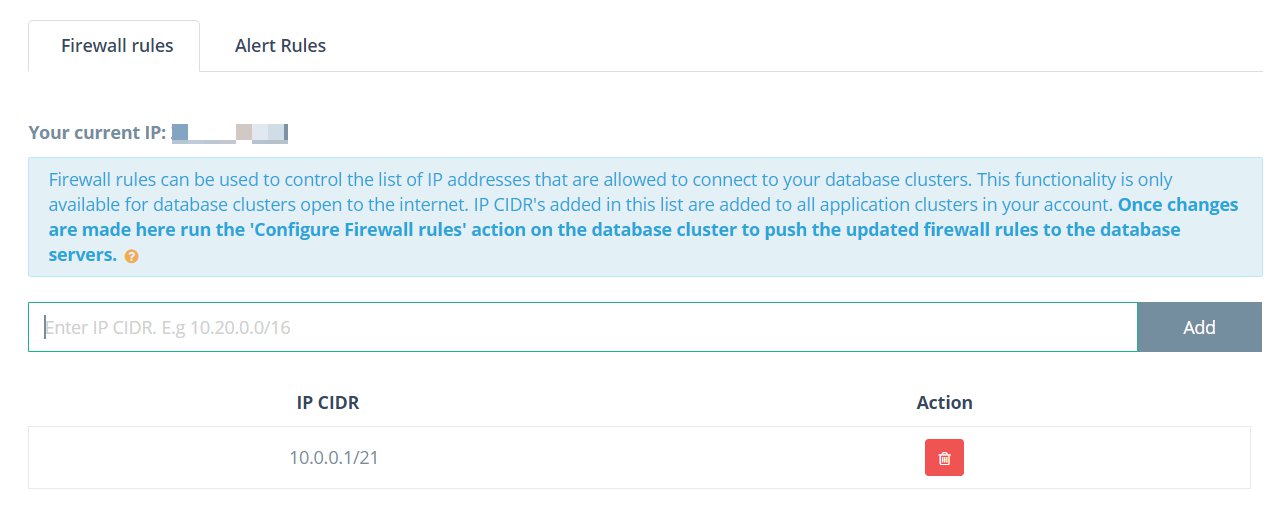
- Once all your IP CIDRs have been added, click the Save button to save the Firewall Rules.
- Note that these rules have still not applied yet. To do so, go to your MongoDB® deployment(s), open the Firewall Modal and press Configure to push the rules to the deployment.
If you have a lot of deployments, you will have to individually go to each deployment and configure the account level rules.
- Once the Firewall Rules have been applied, you should see a green check on the Firewall Rules option on your Cluster Details pages.
Updated 9 months ago
