Setup a GCP Cloud Profile
ScaleGrid allows you to deploy your MySQL, PostgreSQL, Redis™ and MongoDB® database clusters onto your existing Google Cloud Platform (GCP) account in the region of your choice.
Before creating your GCP Cloud Profile, you need to know the following information:
- GCP project ID
- VPC network
- Region
- Subnet
You can find your GCP Project ID from GCP console.
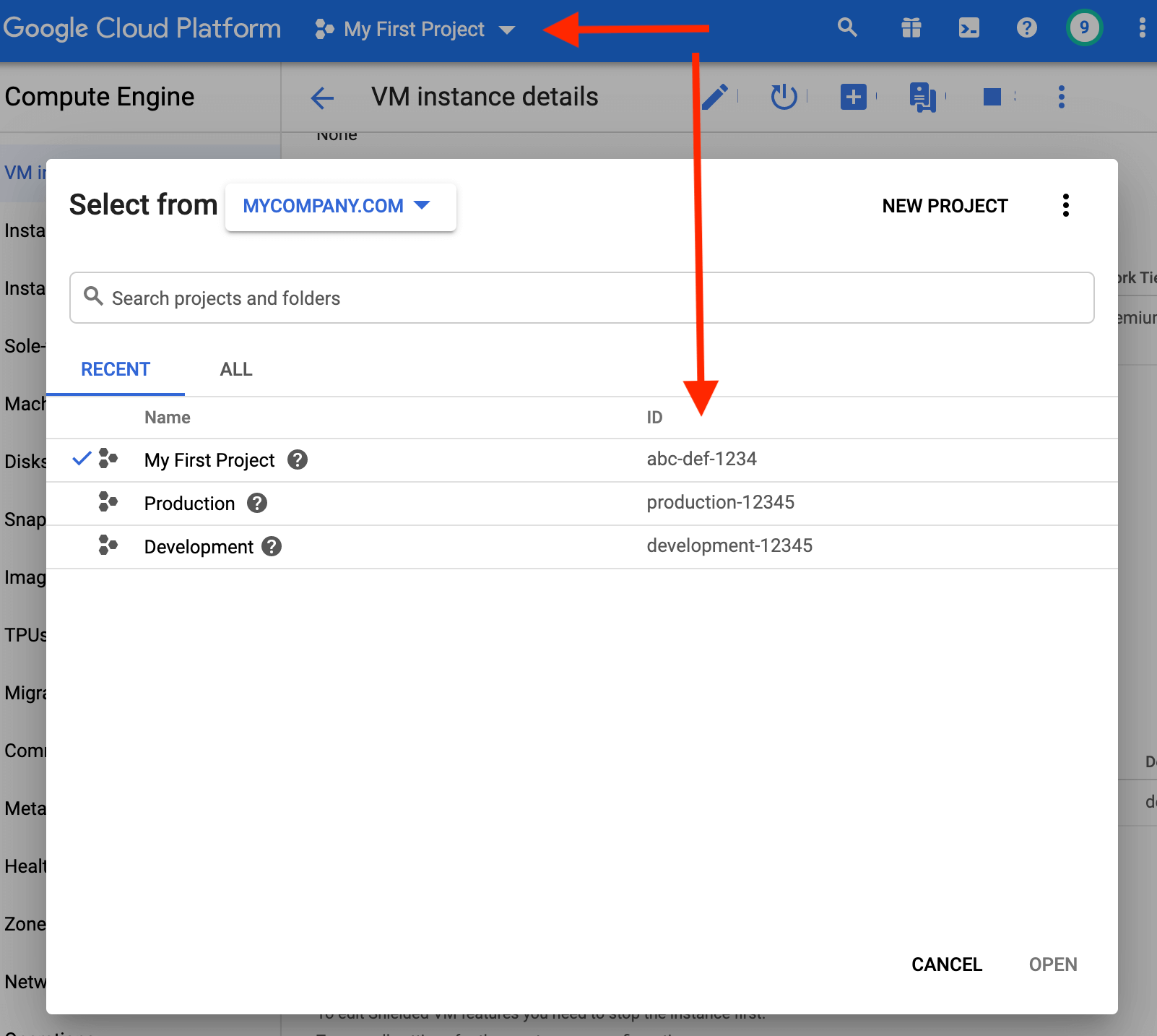
ScaleGrid will create a Service Account, two custom roles, and bind IAM policies to your GCP project with the Service Account and roles. ScaleGrid IAM role details are provided in the IAM Policies, Service Account & Roles section.
Here are the steps for creating a GCP Cloud Profile.
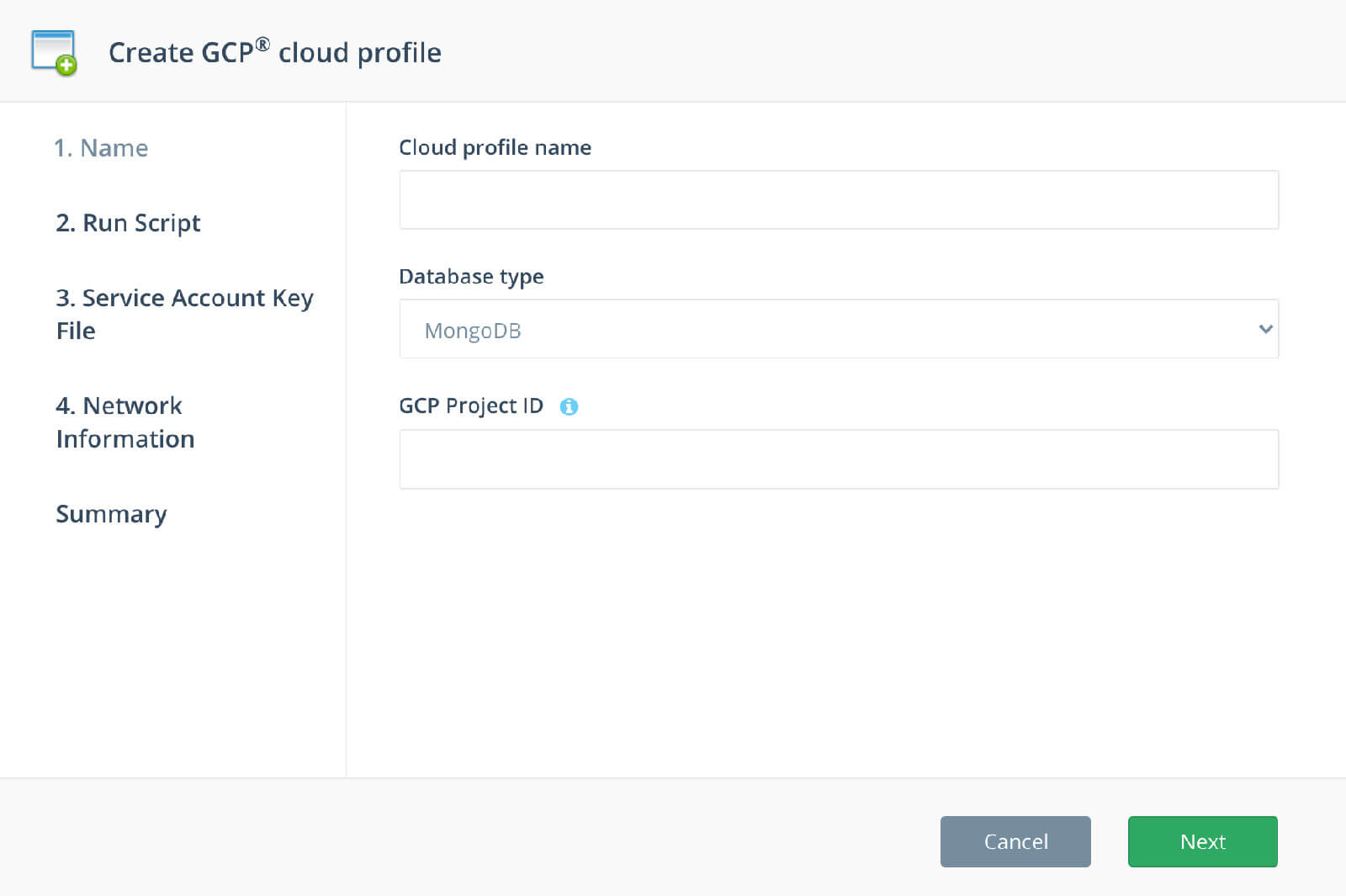
Step 1: Name
Click on the Cloud Profiles link in the left-side menu of the ScaleGrid console, then select the green New Cloud Profile button in the upper right corner of the page. Once the creation wizard opens, enter a Cloud Profile name, select a database type, enter your GCP Project ID, and click Next:
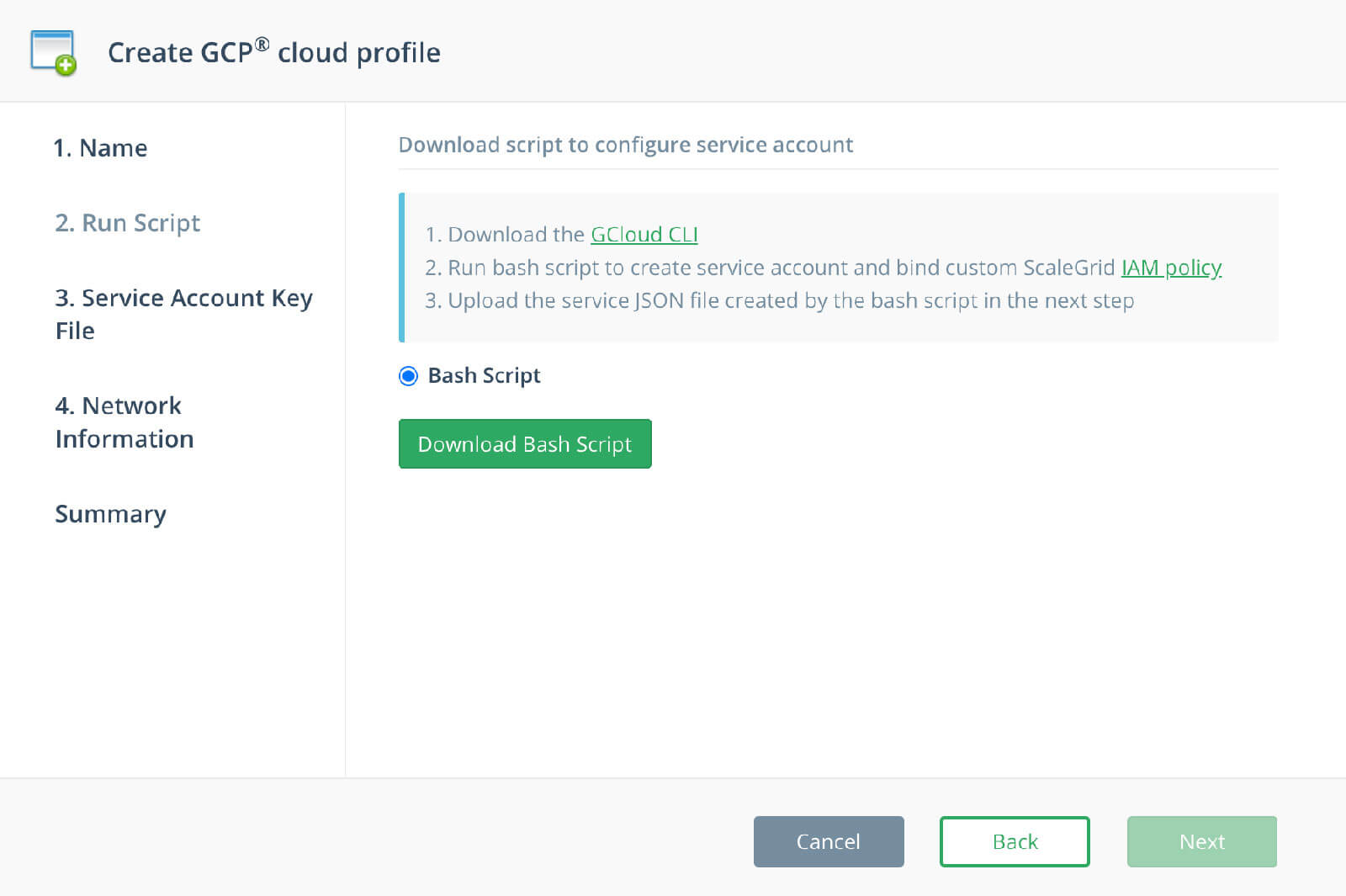
Step 2: Run Script
Download the Bash Script to create a GCP Service Account and bind the custom ScaleGrid IAM policy, and click Next. GCloud CLI is required to run this Bash Script.
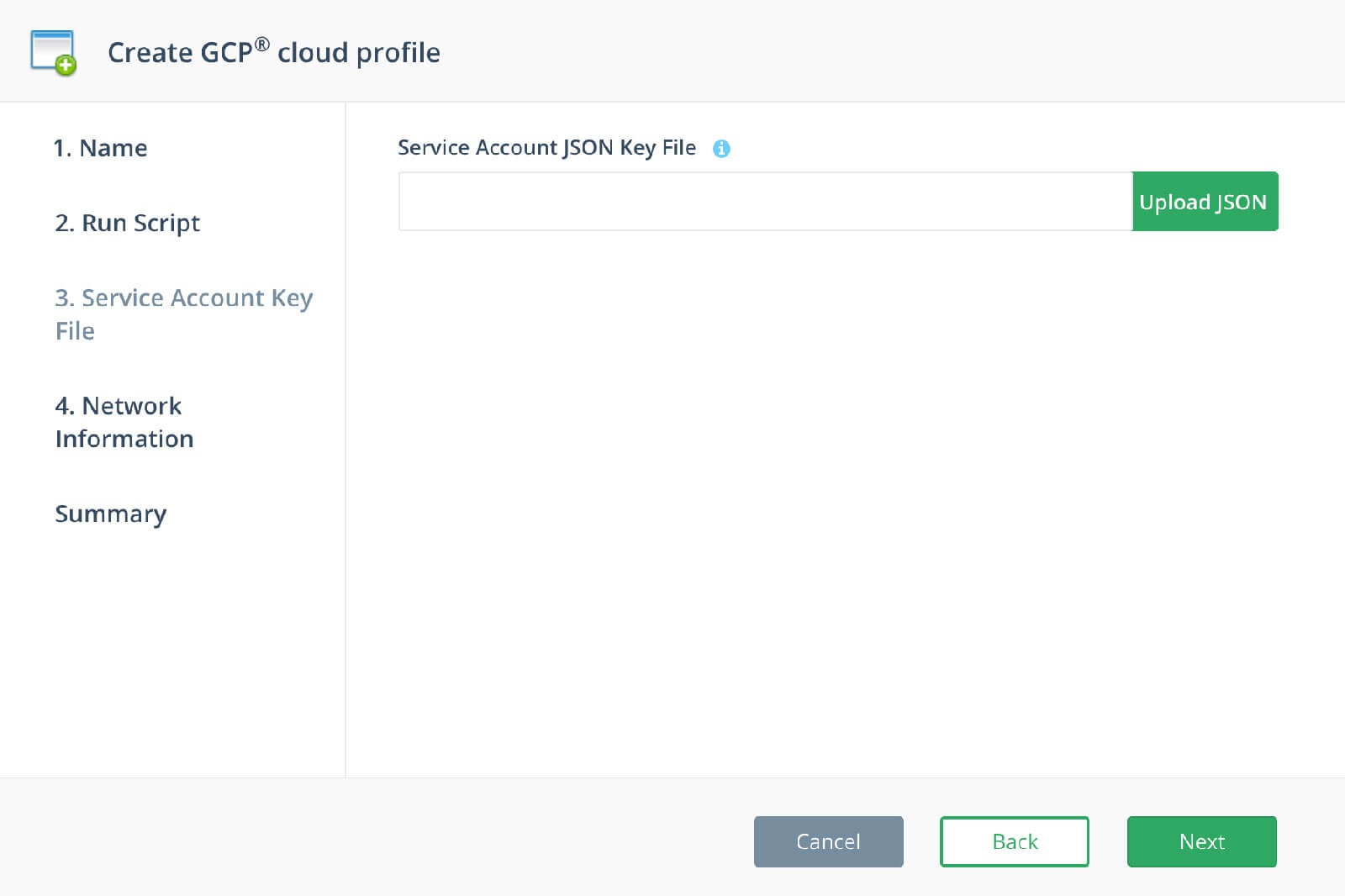
Step 3: Service Account Key File
Upload the Service Account Key File created from the Bash Script and click Next:
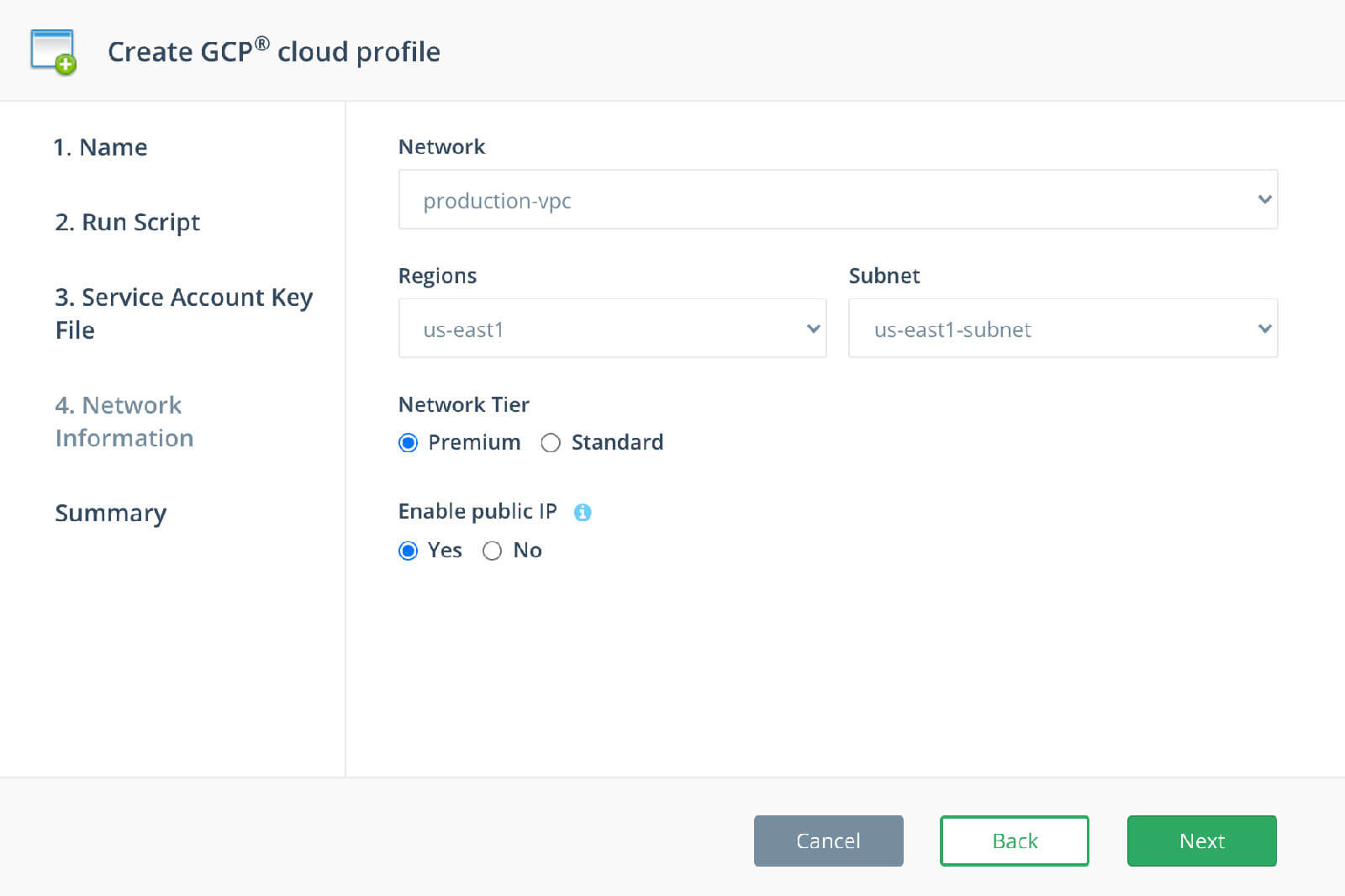
Step 4: Network Information
Select your VPC Network, Region, Subnet and Network Tier. When you Enable Public IP, it will assign a public IP into each of the database cluster’s nodes. Click Next:
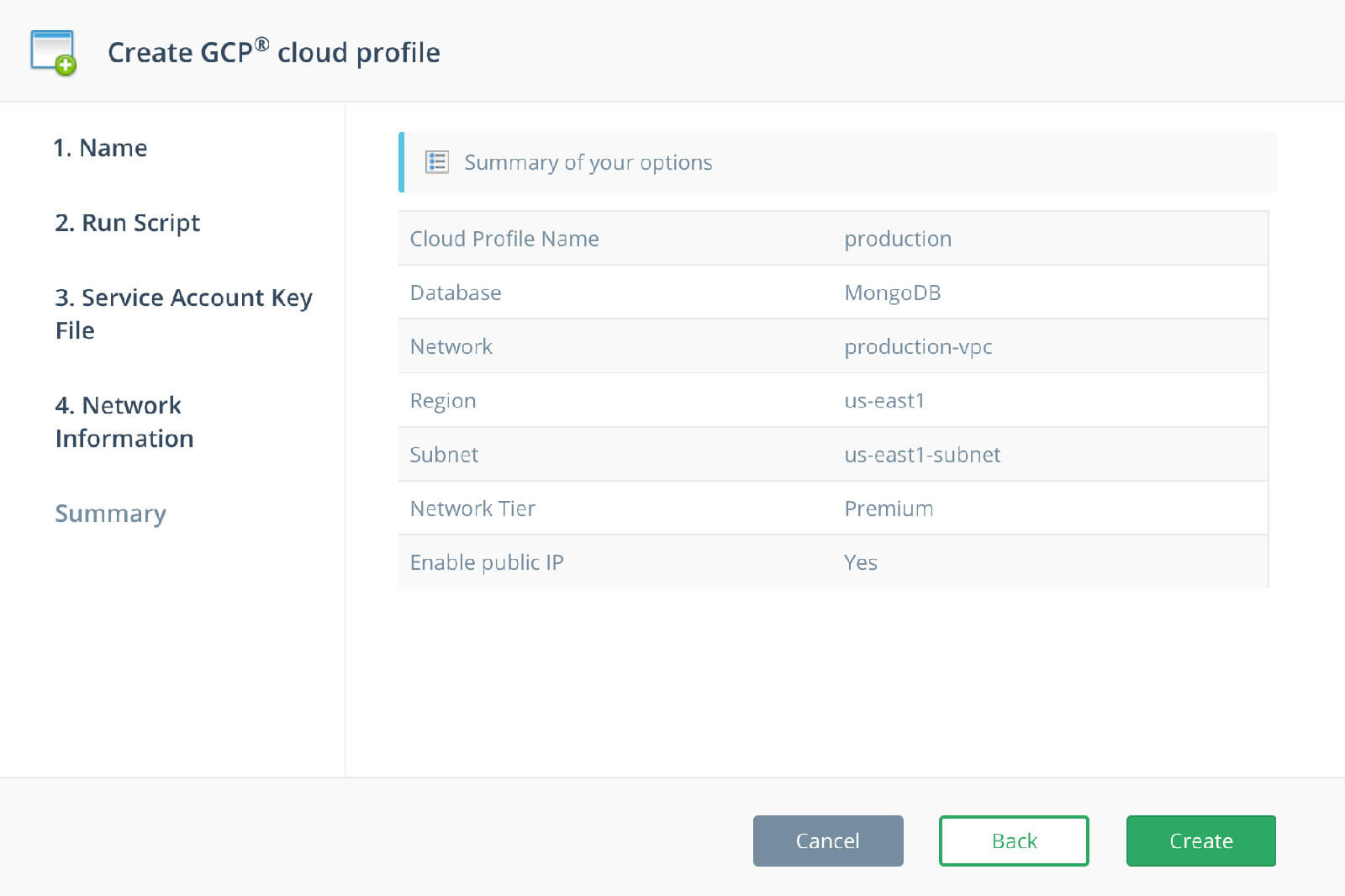
Cloud Profile Summary
The Summary page shows all your selected options. Click the Create button to create your Cloud Profile.
Once your Cloud Profile is created, you will be able to create your first cluster with ScaleGrid.
Notes for GCP Shared VPC
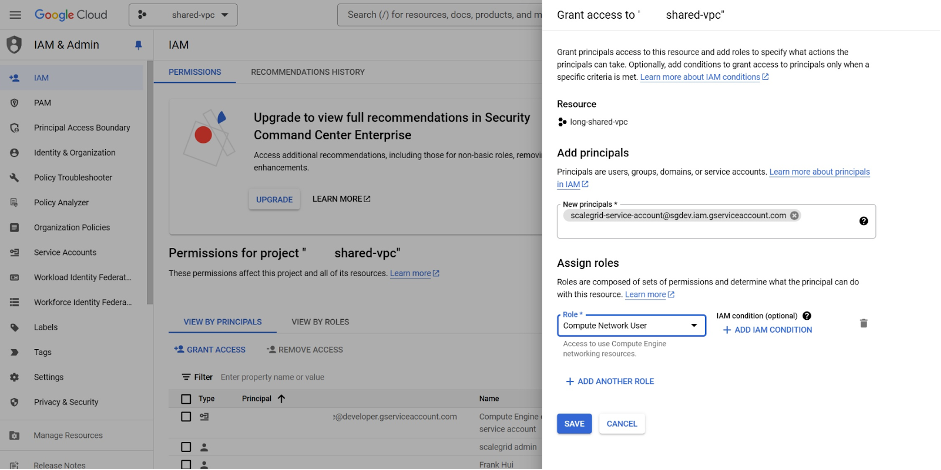
- After running the bash script in Step 2, a service account scalegrid-service-account is created in the service project.
- The account in the service project should have the role of “Compute Network User” in order to use the network resource in the Shared VPC host project.
- Users should assign the role “Compute Network User” to the new service account created in the host project.
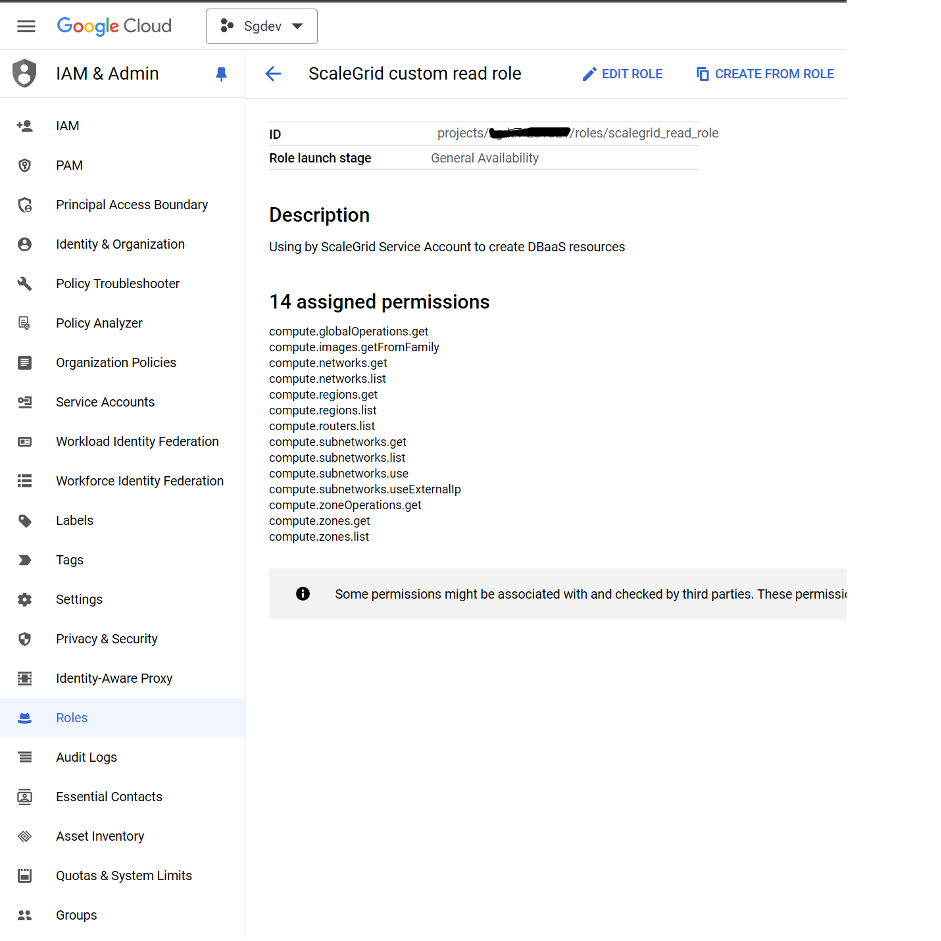
- If the customer has a GCP cloud profile created in Scalegrid before, i.e. the service account has been created already, in addition to the above step, please make sure that the role scalegrid_read_role has the permission compute.projects.get. If you do not see it, please add the permission manually.
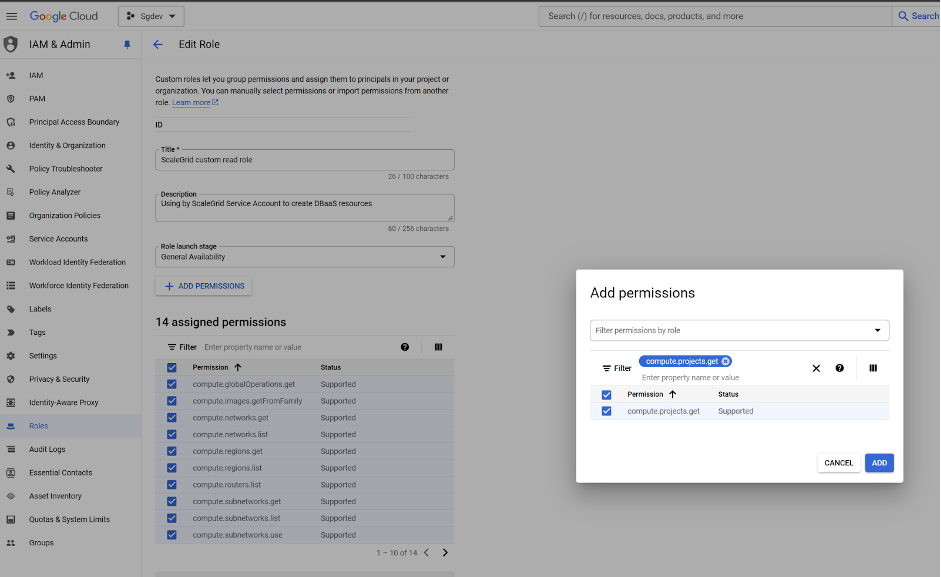
- Please be reminded that the firewall rule should be set up in the Shared VPC network. The following ports should be accessible:
Database Type | Protocol: Port | Type |
|---|---|---|
Mongo | TCP: 27017, 27019 | Ingress |
MySQL | TCP: 3306 | Ingress |
PostgreSQL | TCP: 5432, 6432 | Ingress |
Redis | TCP: 6379, 16379, 26379 | Ingress |
All | TCP: 5671 | Egress |
For the Ingress rule, make sure it is accessible by all the nodes within the cluster.
The Egress rule is for sending heartbeat and monitoring data to the Scalegrid Monitoring system.
IAM Policies, Service Account & Roles
ScaleGrid creates the following resources during Cloud Profile creation:
- Service Account name called scalegrid-service-account in your GCP project.
- Two custom roles:
- scalegrid_write_role
- scalegrid_read_role
- Three IAM policies bindings in your GCP project
- The scalegrid-service-account with scalegrid_read_role.
- The scalegrid-service-account with scalegrid_write_role with condition.
- The scalegrid-service-account with Service Account User role.
Custom Roles
The scalegrid_write_role role contains the following permissions and gives ScaleGrid permissions to modify resources starting with “scalegrid-” or “sg-”.
- compute.globalOperations.get
- compute.images.getFromFamily
- compute.networks.get
- compute.networks.list
- compute.regions.get
- compute.regions.list
- compute.routers.list
- compute.subnetworks.get
- compute.subnetworks.list
- compute.subnetworks.use
- compute.subnetworks.useExternalIp
- compute.zoneOperations.get
- compute.zones.get,compute.zones.list
This role is added to IAM Policy binding with the following condition:
- resource.name.endsWith( resource.name.extract( "sg-{end}") ) ||
- resource.name.endsWith( resource.name.extract( "scalegrid-{end}") ) ||
- resource.name.endsWith( - resource.name.extract( "/global/networks/{end}" ) )
The scalegrid_read_role contains the following permissions and gives ScaleGrid permission to read the account configuration which is used to set up the Cloud Profile.
- compute.globalOperations.get
- compute.images.getFromFamily
- compute.networks.get
- compute.networks.list
- compute.projects.get
- compute.regions.get
- compute.regions.list
- compute.routers.list
- compute.subnetworks.get
- compute.subnetworks.list
- compute.subnetworks.use
- compute.subnetworks.useExternalIp
- compute.zoneOperations.get
- compute.zones.get,compute.zones.list
Updated 9 months ago
