Setup an Oracle Cloud Infrastructure (OCI) Cloud Profile
ScaleGrid allows you to deploy your MySQL, PostgreSQL, Redis™ and MongoDB® database clusters onto your existing Oracle Cloud Infrastructure (OCI) account in your subscribed region.
Identity and Access setup
You need to create an OCI user with API key and then add it into a new OCI group. Then create a tag namespace called ScaleGrid in your home region root tenancy. Moreover, you need to create policy rules in your root compartment and compartment(s) which deploy ScaleGrid database server(s). Finally, you must have at least 1 VCN with a public or private subnet which has a route to Internet and a network security group for creating a cloud profile in ScaleGrid.
Step 1: Setup a user, API key & group for ScaleGrid
Create a user
Steps to create a user:
- Go to Identity & Security > Users page.
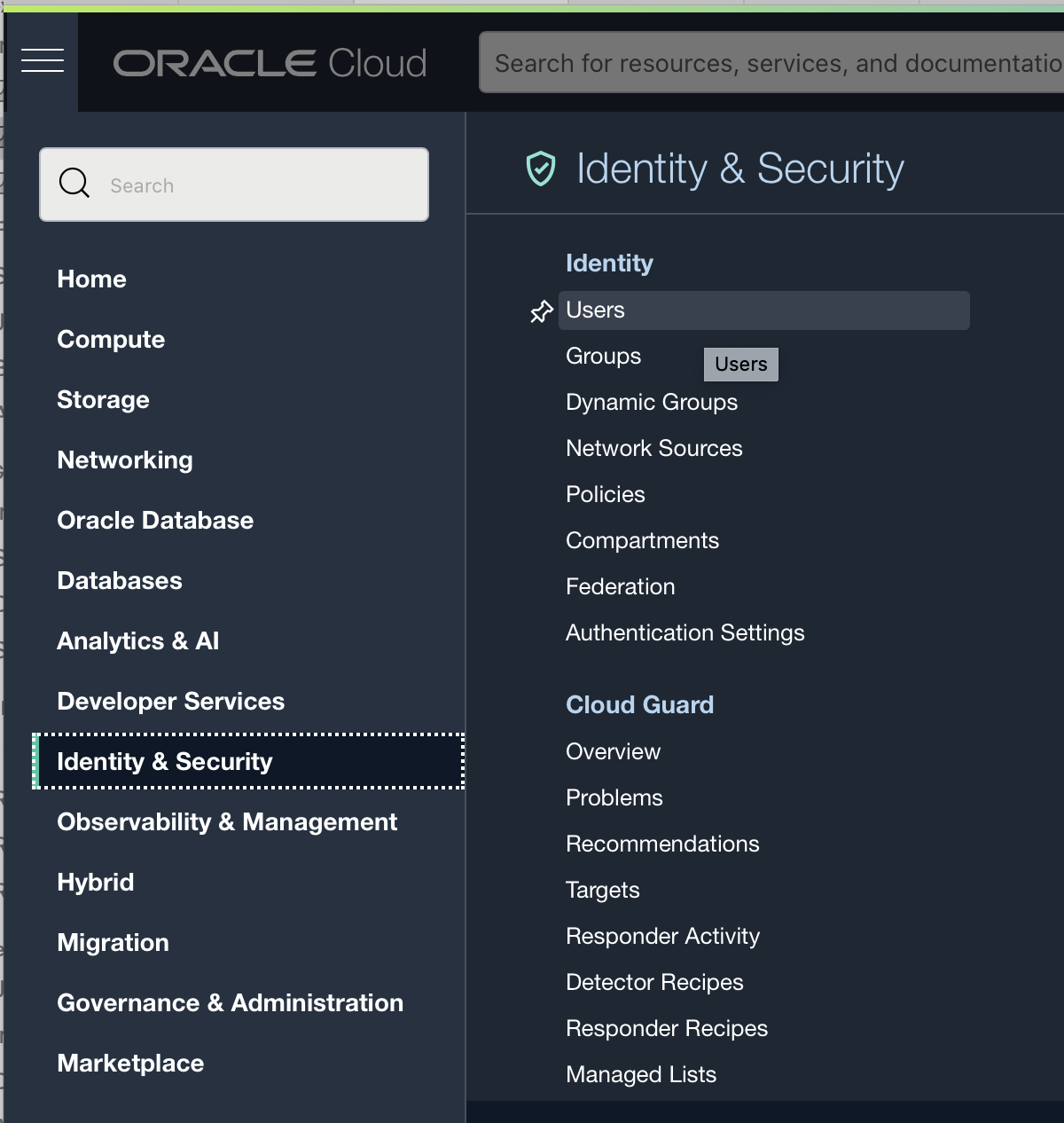
- Click the Create User button to create a new user.
Add user API key
Before adding the API key, you need to generate an API signing key. Please keep your public and private keys in a safe place. We need both keys in later steps.
Steps to add user API key
- Login to OCI Console.
- Select your Home Region.
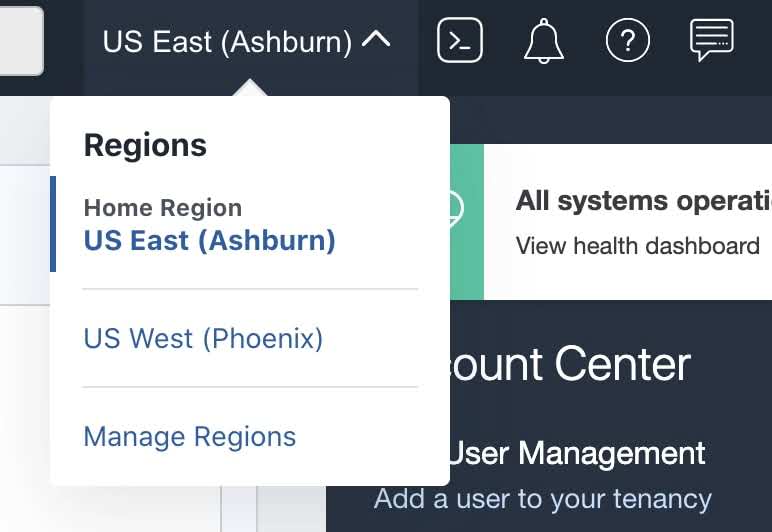
- Go to Identity & Security > Users page
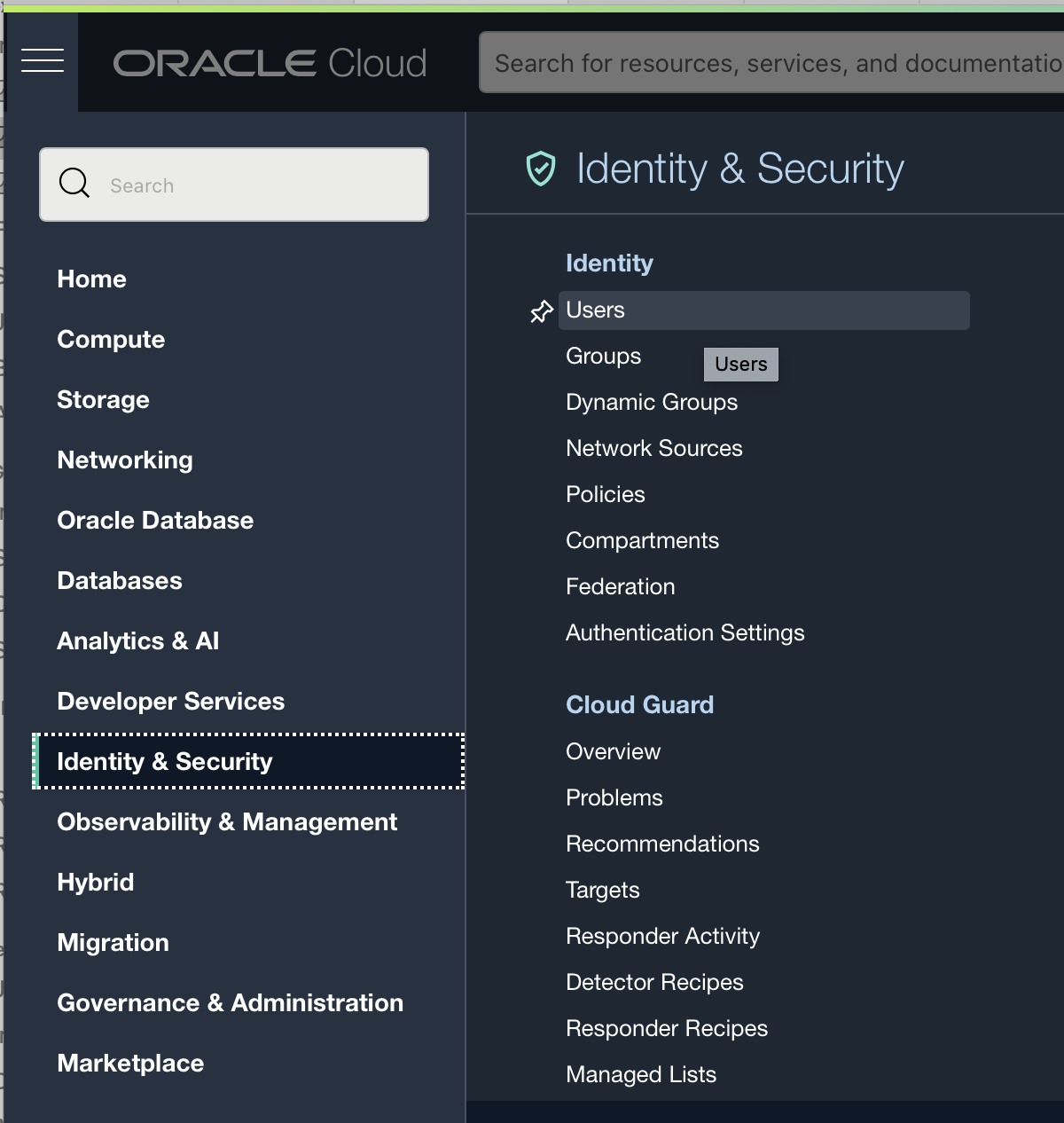
- Click the user that you have created in the previous step.
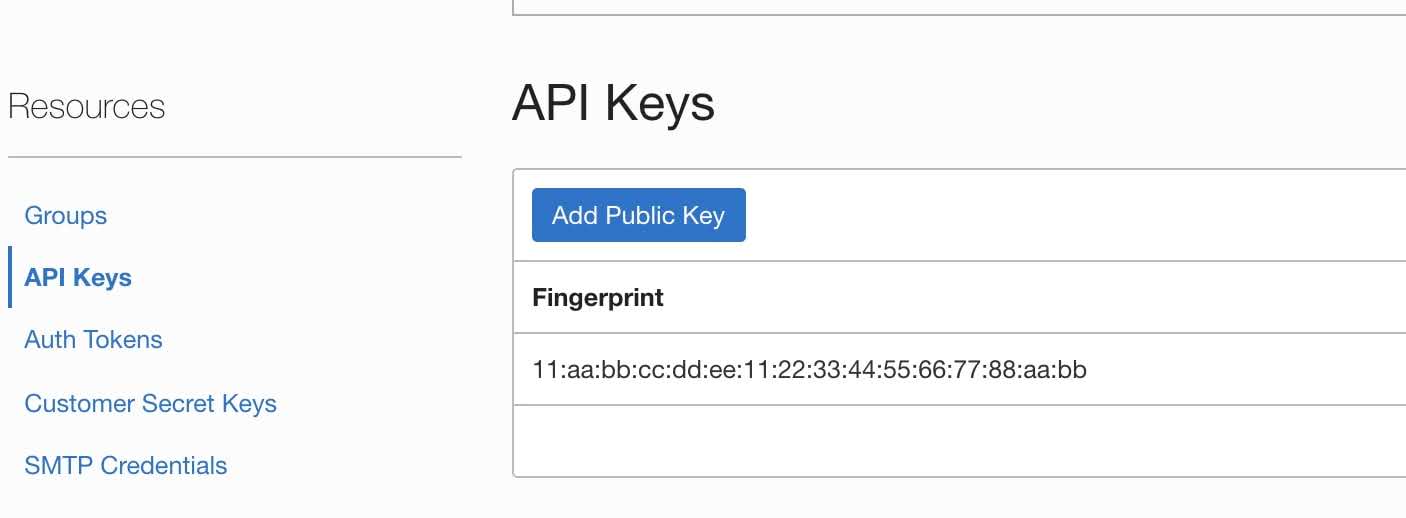
- Click API Keys under the Resources section on the bottom left of the page.
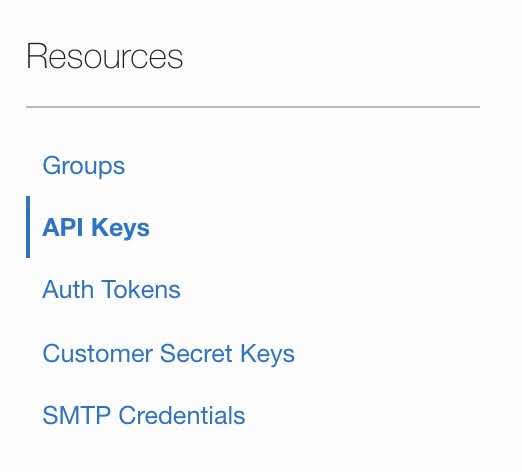
- Click the Add API Key button select the PASTE PUBLIC KEYS radio button then paste your public key into the PUBLIC KEY text area.
- Click the Add button.
- Please copy the Fingerprint form the API Keys section. We will need this to create the cloud profile in ScaleGrid.
Create a group
Steps to create a group:
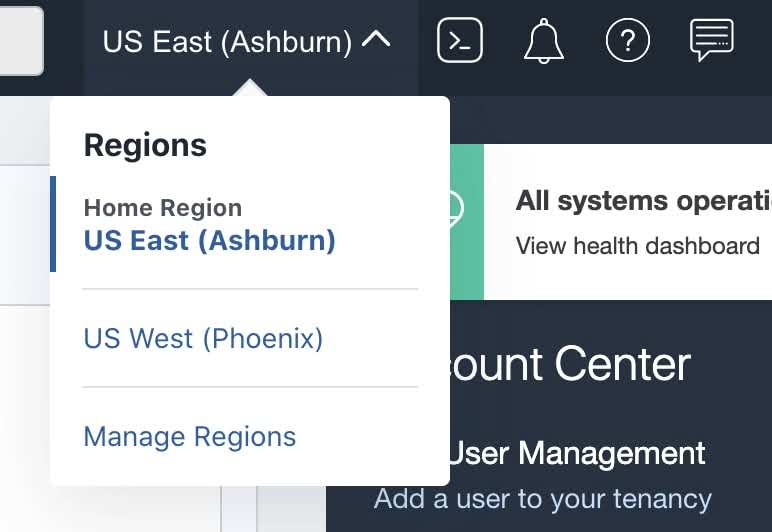
- Login to OCI Console.
- Select your Home Region
- Go to Identity & Security > Groups page.
- Click the Create Group button to create a new group
Add user to group
Steps to add user into the group:
- Go to Identity & Security > Groups page.
- Click the group that you have created in the create group step.
- Click the Add User to Group button.
- Select the user that you have created in the create user step then click the Add button.
Step 2: Setup ScaleGrid compartment(s) and tag namespace
Create a compartment
Steps to create a compartment
- Go to Identity & Security > Compartments page.
- Click the Create Compartment button.
- Fill in both Name and Description then select your root compartment.
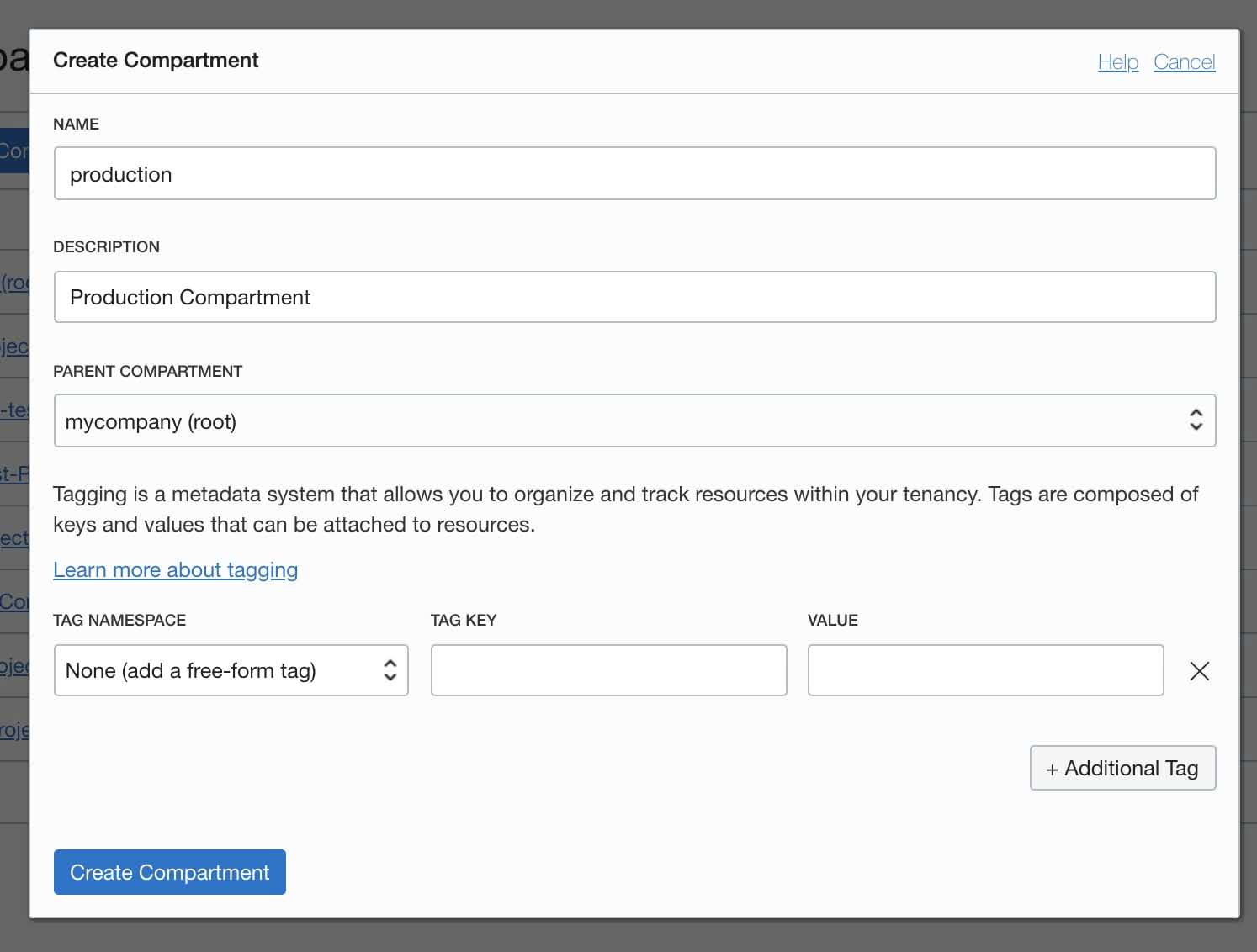
- Click the Create Compartment button.
Create tag namespace
You can create the Tag namespace called ScaleGrid in your root tenancy or you can create your own Tag name same in your Compartment.
If the ScaleGrid Tag namespace is created in root tenancy then you must have the following IAM policy.
Allow group <Group name> to use tag-namespaces in tenancy
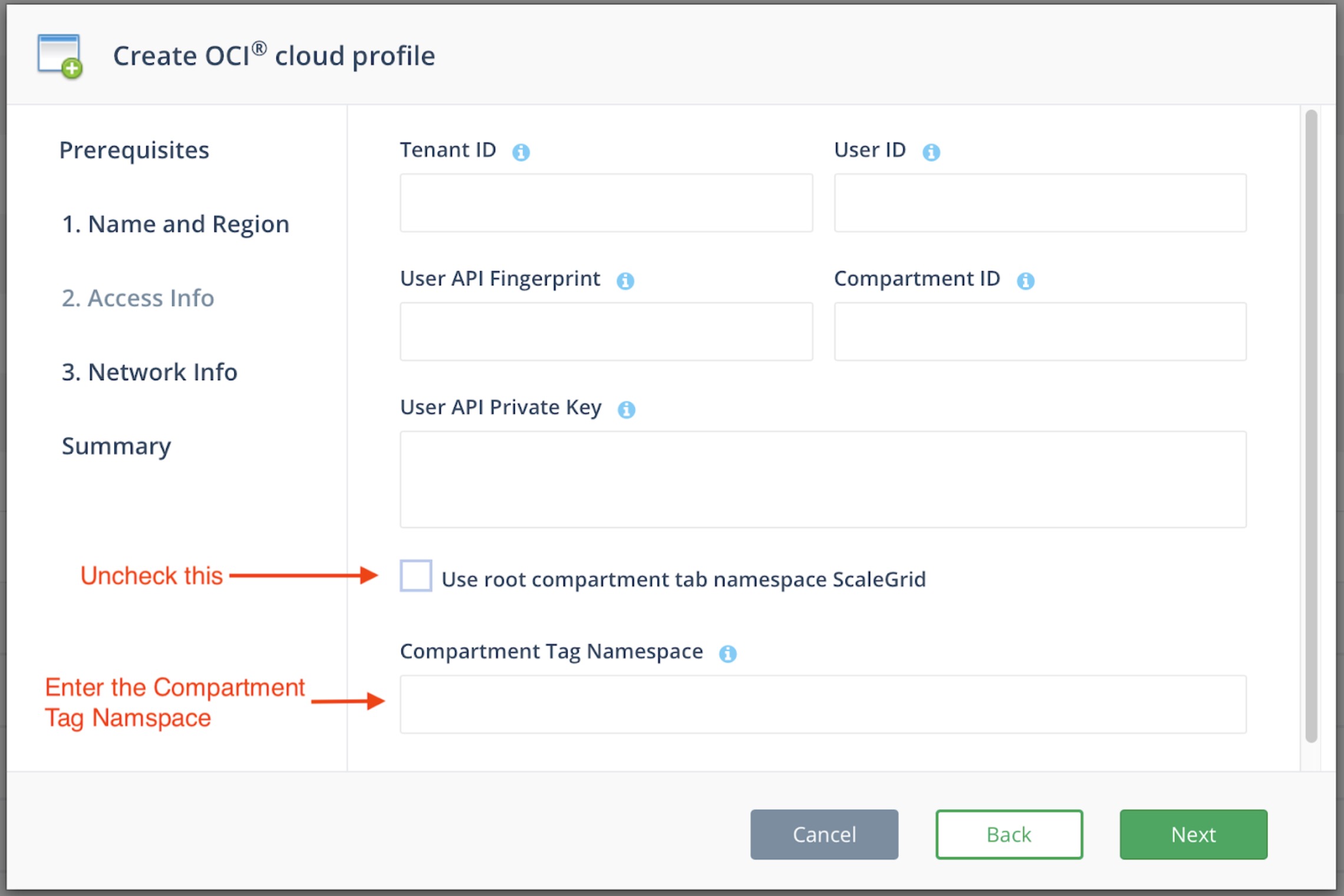
If you want to define your own Tag namespace in your Compartment then you don’t require the above policy but you need to provide the Tag namespace name during cloud profile creation Step 2 - Access Info.
Steps to create tag namespace
- Go to Governance & Administration > Tag Namespaces page.
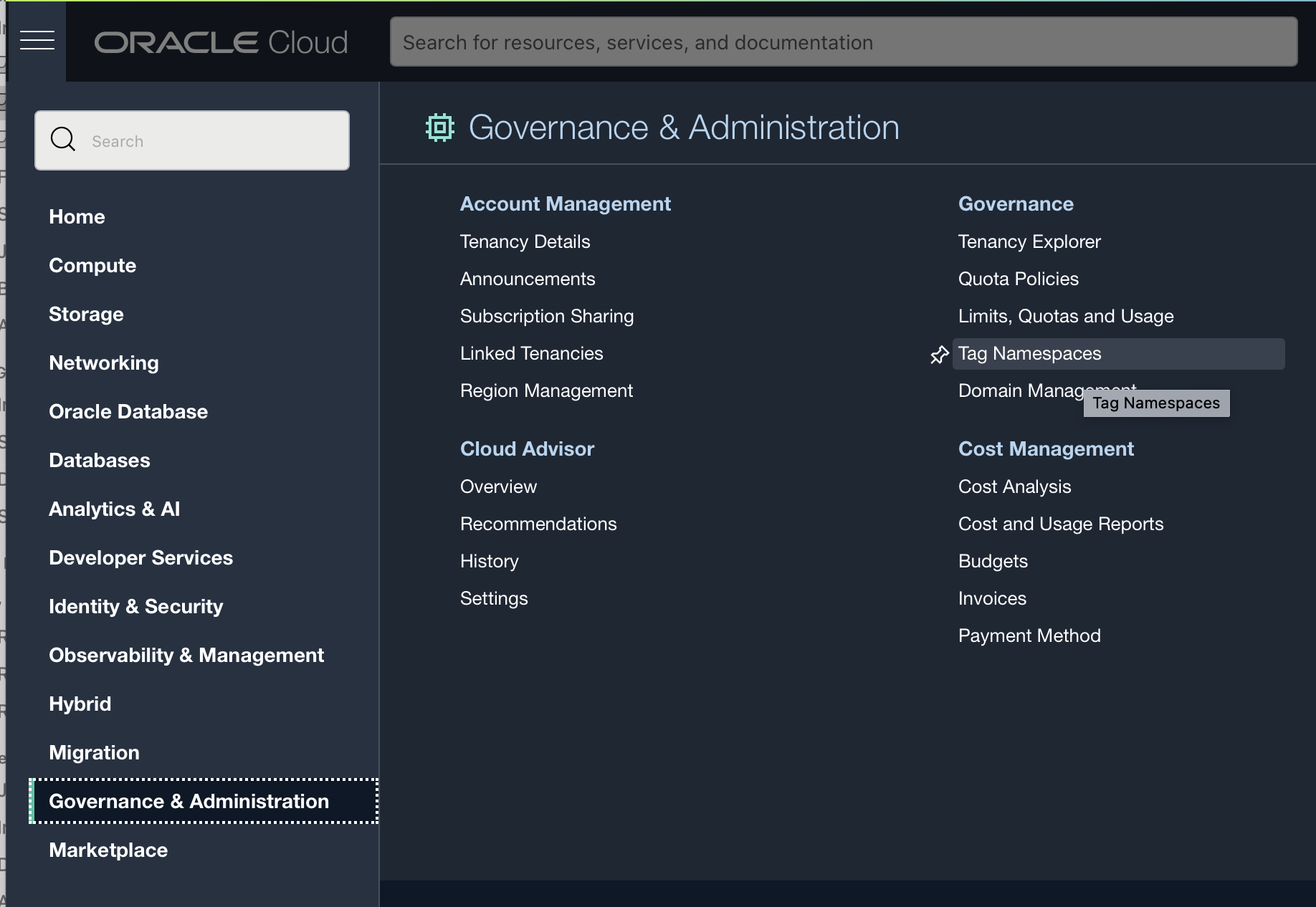
- Click the Create Namespace Definition button.
- Fill in the following information in Create Namespace Definition dialog box:
--Select root compartment (or your Compartment) from CREATE IN COMPARTMENT dropdown.
--Enter ScaleGrid (or an appropriate name for your Compartment Tag Namespace) in NAMESPACE DEFINITION NAME text box.
--Enter For ScaleGrid in DESCRIPTION text box.
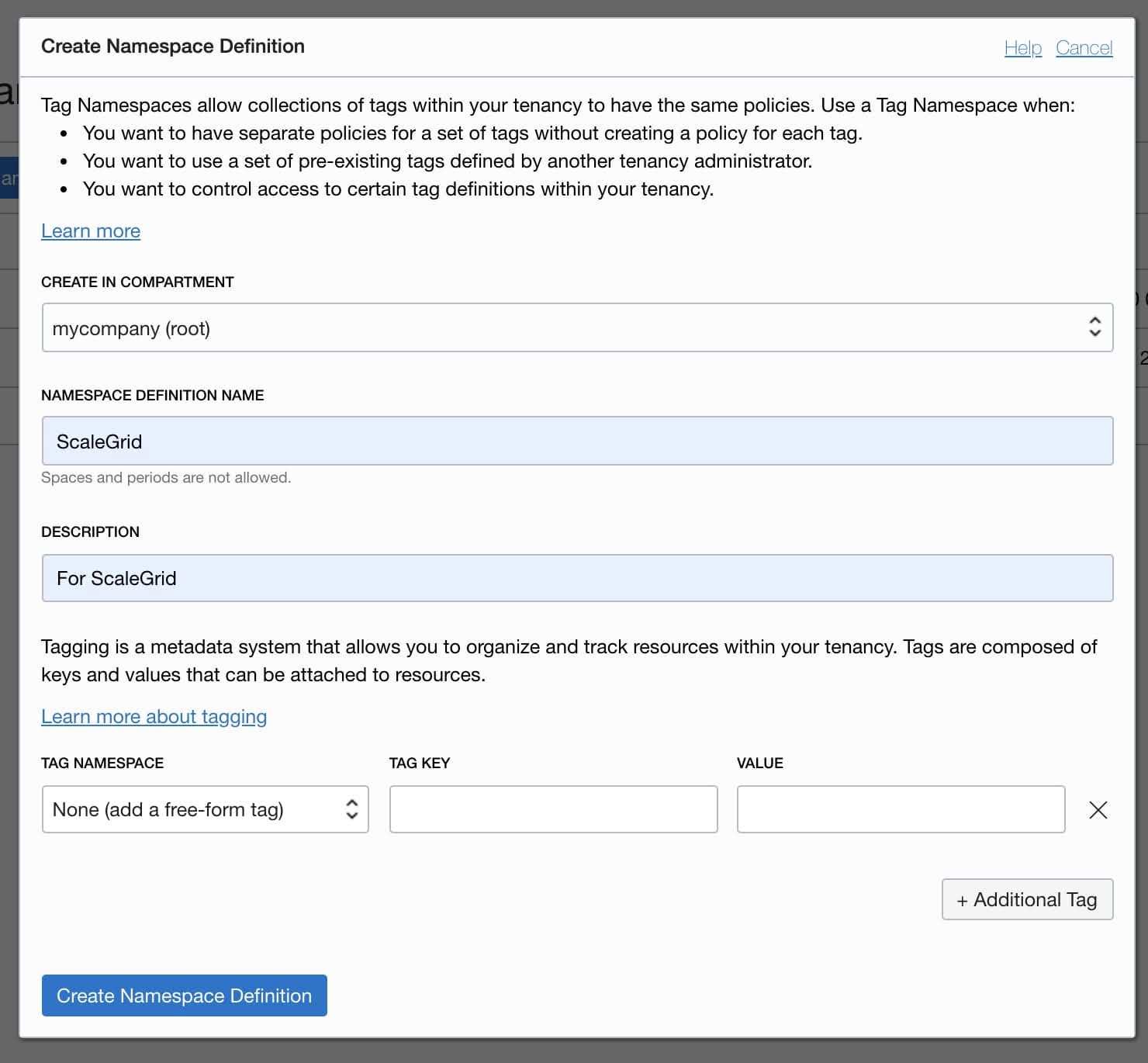
- Click the Create Namespace Definition button.
- Go back to the Tag Namespaces page and click the ScaleGrid tag namespace.
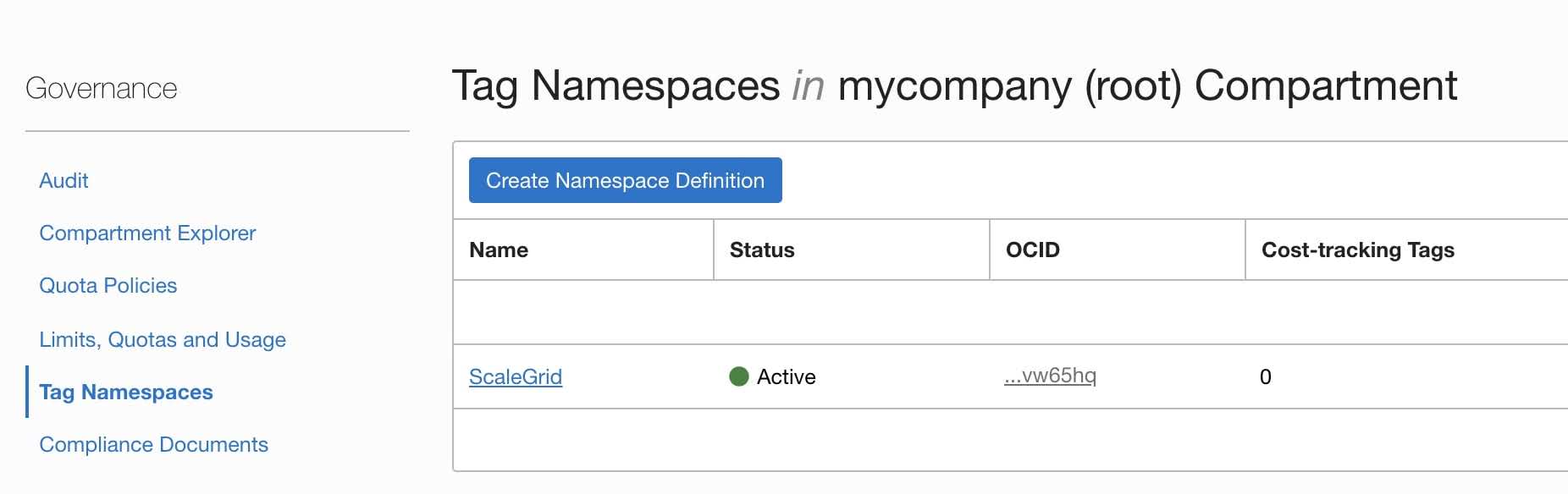
- Click the Create Tag Key Definition button.
- Fill in the following information in Create Tag Key Definition dialog box:
--Enter DBProvider in TAG KEY text box.
--Enter For ScaleGrid in DESCRIPTION text box. - Click the Create Tag Key Definition button.
Step 3: Setup ScaleGrid IAM Policy for Compartment & tag namespace
Optional: Create a root tenancy policy
NOTE: You only need to configure a root renancy policy if you would like to use ScaleGrid with one consistent tag namespace across multiple Oracle compartments. If you want to configure a ScaleGrid Cloud profile only using compartment level policies, you will need to create a unique tag namespace for each compartment you associate with a ScaleGrid Cloud profile.
Steps to create a root tenancy policy
- Login to OCI Console.
- Select your Home Region.
- Go to Identity & Security > Policies page.
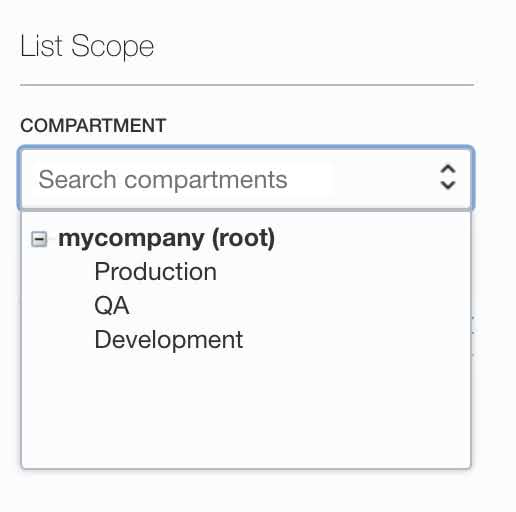
- Select root compartment from COMPARTMENT dropdown in List Scope section.
- Click the Create Policy button.
- Fill in the following information:
--Enter ScaleGrid in the NAME text box.
--Enter For ScaleGrid in the DESCRIPTION text box.
--Select your root compartment.
--Click Show manual editor in Policy Builder box.
Root tenancy policy rules for ScaleGridReplace
<Group name>with the group name that you have created in the previous step.
Allow group <Group name> to use tag-namespaces in tenancy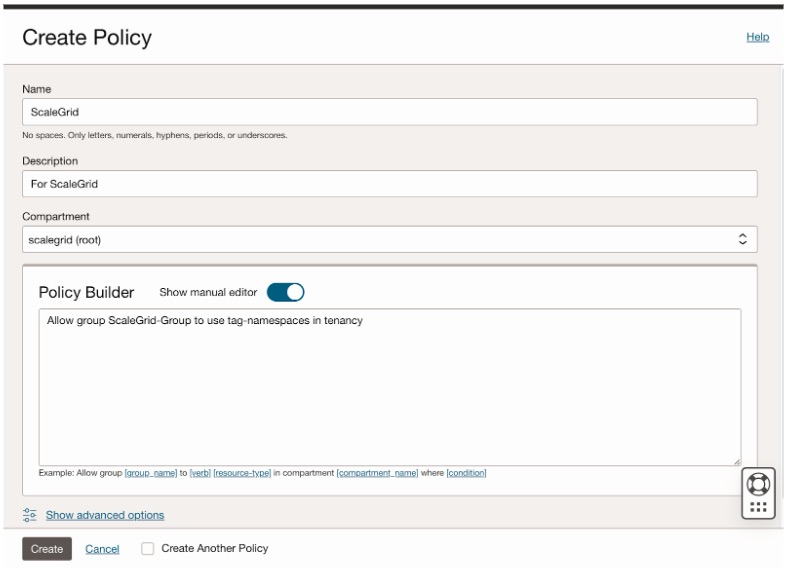
- Click the Create button.
Create a compartment policy
Steps to create a compartment policy for ScaleGrid
- Go to Identity & Security > Policies page.
- Select the compartment for your ScaleGrid cloud profile from COMPARTMENT dropdown in List Scope section.
- Click the Create Policy button.
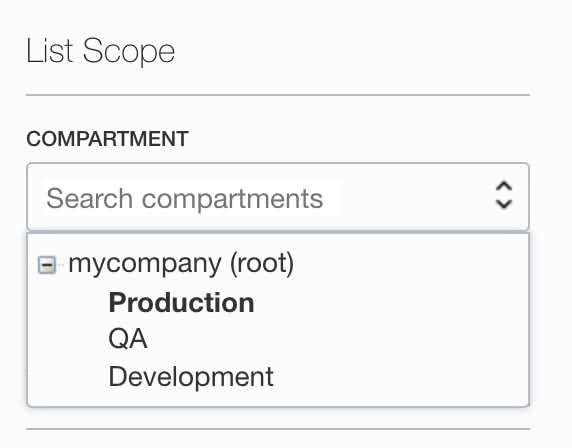
- Fill in the following information:
--Enter a policy name in the NAME text box.
--Enter For ScaleGrid in the DESCRIPTION text box.
--Select your compartment (not root).
--Click Show manual editor in Policy Builder box
Compartment policy rules for ScaleGridReplace
<Group name>with the group name that you have created in the previous step.
Replace<Compartment name>with the compartment of your choice, but not root.
Allow group <Group name> to inspect vcns in compartment <Compartment name>
Allow group <Group name> to inspect route-tables in compartment <Compartment name>
Allow group <Group name> to read instance-images in compartment <Compartment name>
Allow group <Group name> to manage app-catalog-listing in compartment <Compartment name>
Allow group <Group name> to use vnics in compartment <Compartment name>
Allow group <Group name> to use vnic-attachments in compartment <Compartment name>
Allow group <Group name> to use subnets in compartment <Compartment name>
Allow group <Group name> to manage volume-attachments in compartment <Compartment name>
Allow group <Group name> to use volumes in compartment <Compartment name> where target.resource.tag.<Tag namespaces>.DBProvider = 'ScaleGrid'
Allow group <Group name> to inspect volumes in compartment <Compartment name>
Allow group <Group name> to manage volumes in compartment <Compartment name> where request.operation = 'CreateVolume'
Allow group <Group name> to manage volumes in compartment <Compartment name> where target.resource.tag.<Tag namespaces>.DBProvider = 'ScaleGrid'
Allow group <Group name> to manage volume-backups in compartment <Compartment name> where request.operation = 'CreateVolumeBackup'
Allow group <Group name> to manage volume-backups in compartment <Compartment name> where target.resource.tag.<Tag namespaces>.DBProvider = 'ScaleGrid'
Allow group <Group name> to read volume-backups in compartment <Compartment name>
Allow group <Group name> to manage instances in compartment <Compartment name> where ANY { request.operation = 'LaunchInstance', request.permission = 'INSTANCE_UPDATE', target.resource.tag.<Tag namespaces>.DBProvider = 'ScaleGrid'}
Allow group <Group name> to inspect instances in compartment <Compartment name>
Allow group <Group name> to use network-security-groups in compartment <Compartment name>
Allow group <Group name> to manage network-security-groups in compartment <Compartment name> where request.operation = 'AddNetworkSecurityGroupSecurityRules'
Allow group <Group name> to inspect all-resources in compartment <Compartment name>
Allow group <Group name> to use tag-namespaces in compartment <Compartment name>
- Click the Create button.
Step 4: Setup VCN, Subnet(s), NSG & Gateway(s)
You need to have 1 VCN with a public or private subnet which has a route to Internet and a network security group for creating a cloud profile in ScaleGrid.
Create VCN, Subnet and Route using VCN Wizard
The easiest way to create a virtual cloud network (VCN), public & private subnets, and default route is to use OCI console Start VCN Wizard.
Steps to create VCN, Subnet and Route
- Login to OCI console.
- Select your region.
- Go to Networking > Virtual Cloud Networks page.
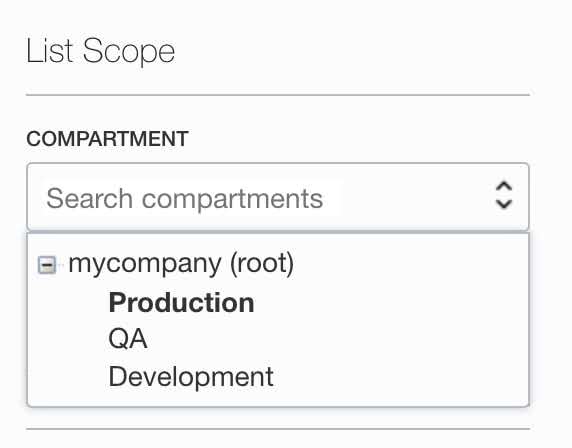
- Select your compartment under the List Scope section from the left bottom page.
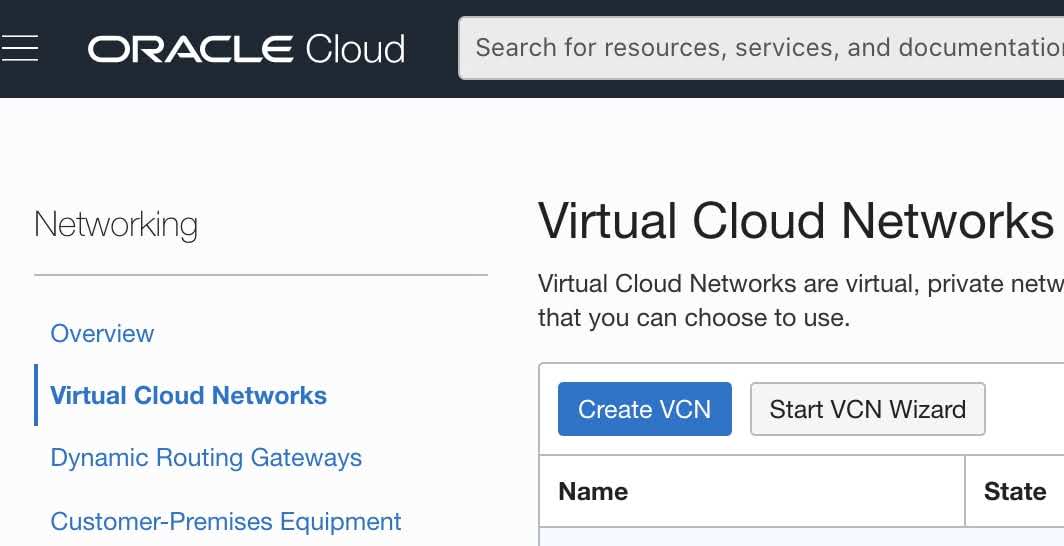
- Click the Start VCN Wizard button.
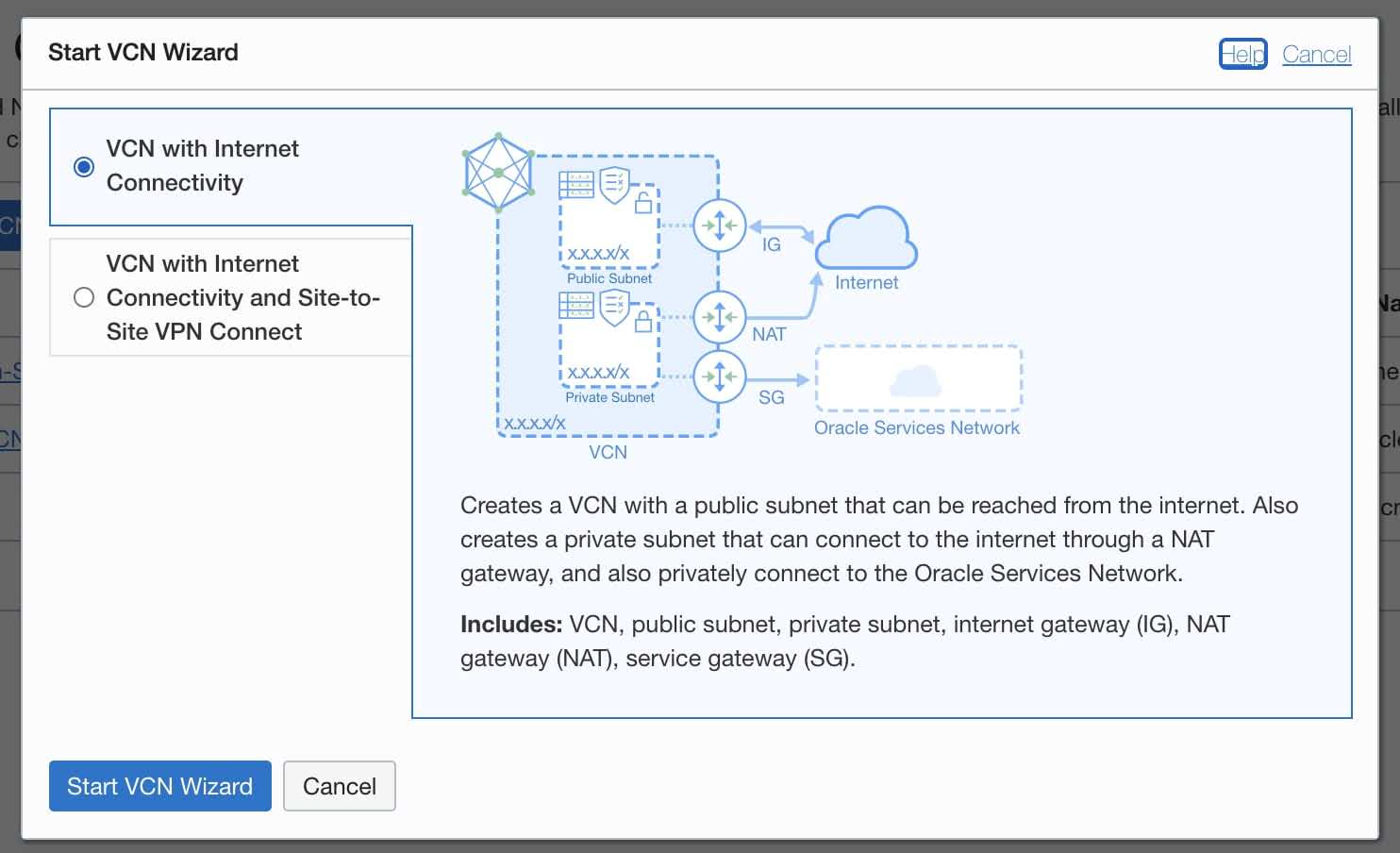
- Select VCN with Internet Connectivity radio button then click the Start VCN Wizard button.
- Fill in the VCN name and select your compartment created in the previous step.
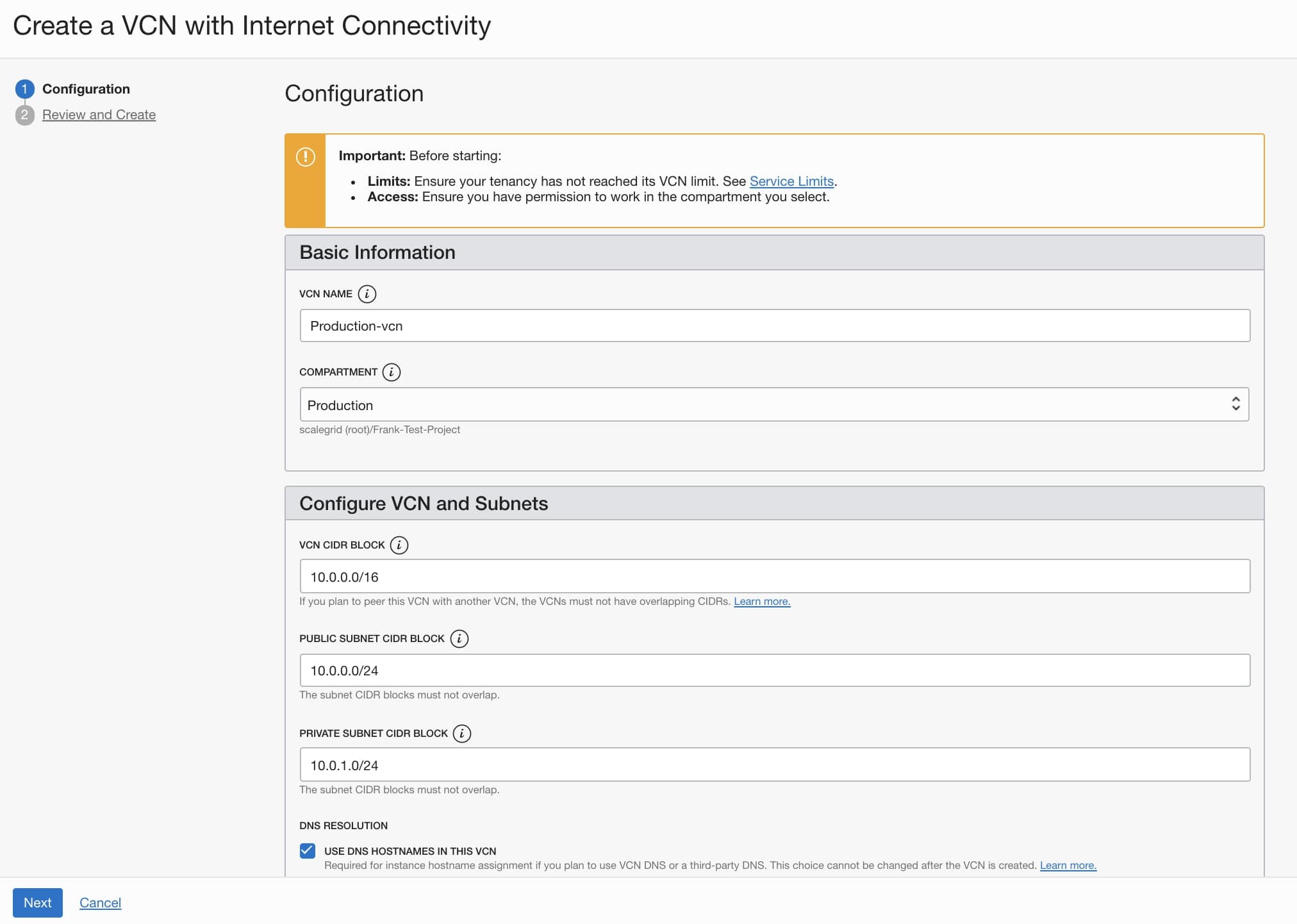
- Click the Next button.
- Click the Create button.
Subnet Route to Internet
All database clusters’ nodes (VMs) by ScaleGrid must have internet access.
For public subnet, it must have a route rule to the Internet Gateway.
For private subnet, it must have a NAT Gateway.
Steps to check public subnet has route to Internet
- Go to Networking > Virtual Cloud Networks page.
- Select your compartment under the List Scope section from the left bottom page.
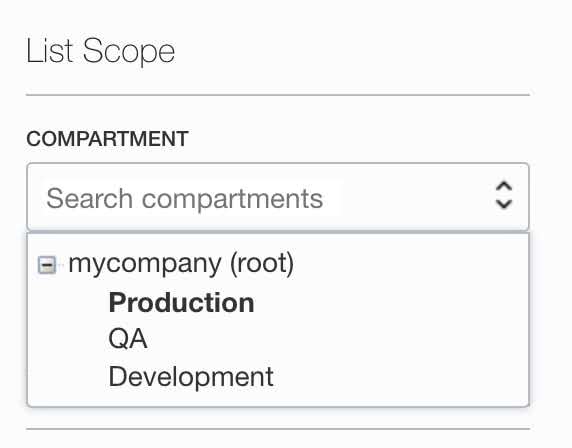
- Click your VCN.
- Click Subnets under the Resources section from the left.
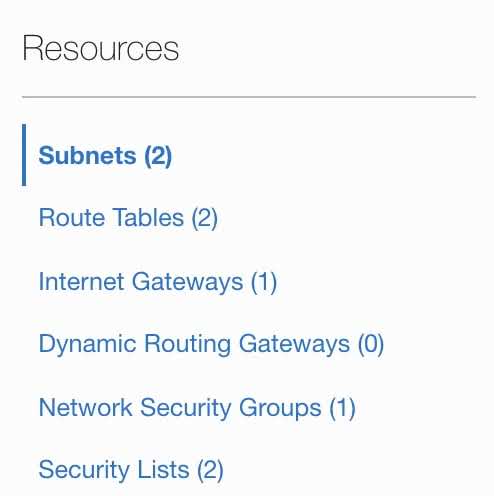
- Click your public subnet.
- Click the Route Table link.
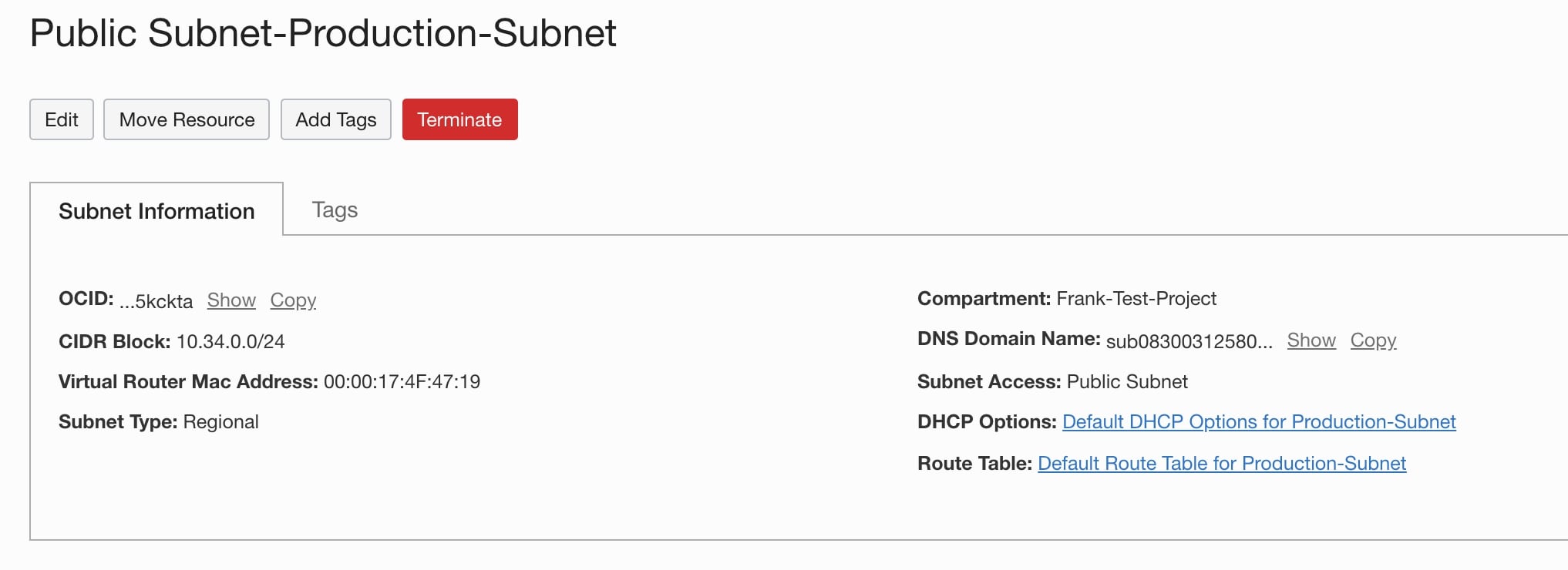
You should expect to see an Internet Gateway route rule.
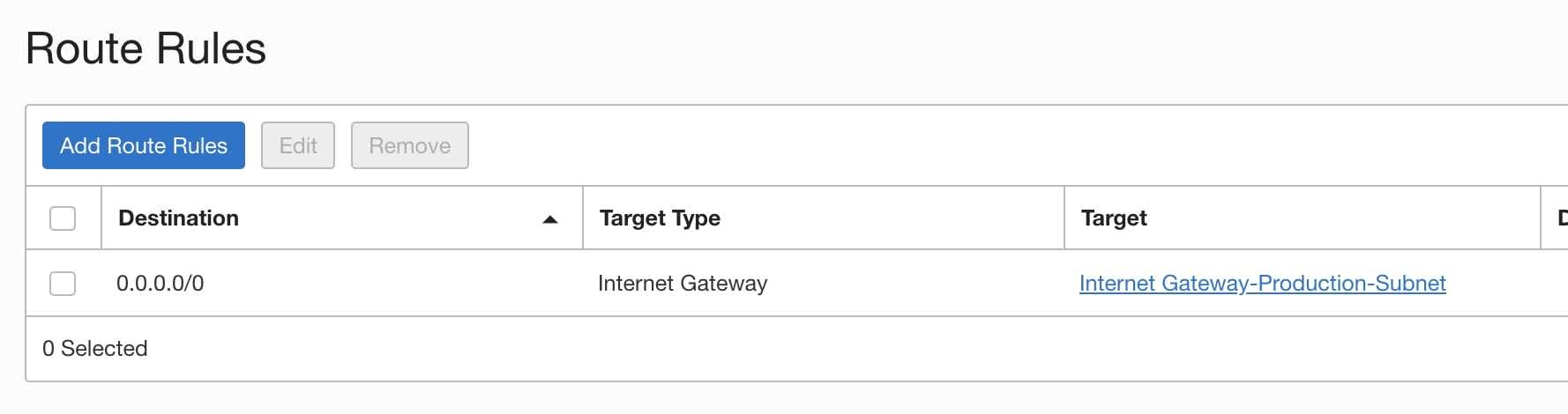
If you don’t have the above route rule then please create an internet gateway and add the route rule to your subnet route table. You can find more details from here.
Steps to check private subnet has route to Internet
- Go to Networking > Virtual Cloud Networks page.
- Select your compartment under the List Scope section from the left bottom page.
- Click your VCN.
- Click Subnets under the Resources section from the left.
- Click your private subnet.
- Click the Route Table link.
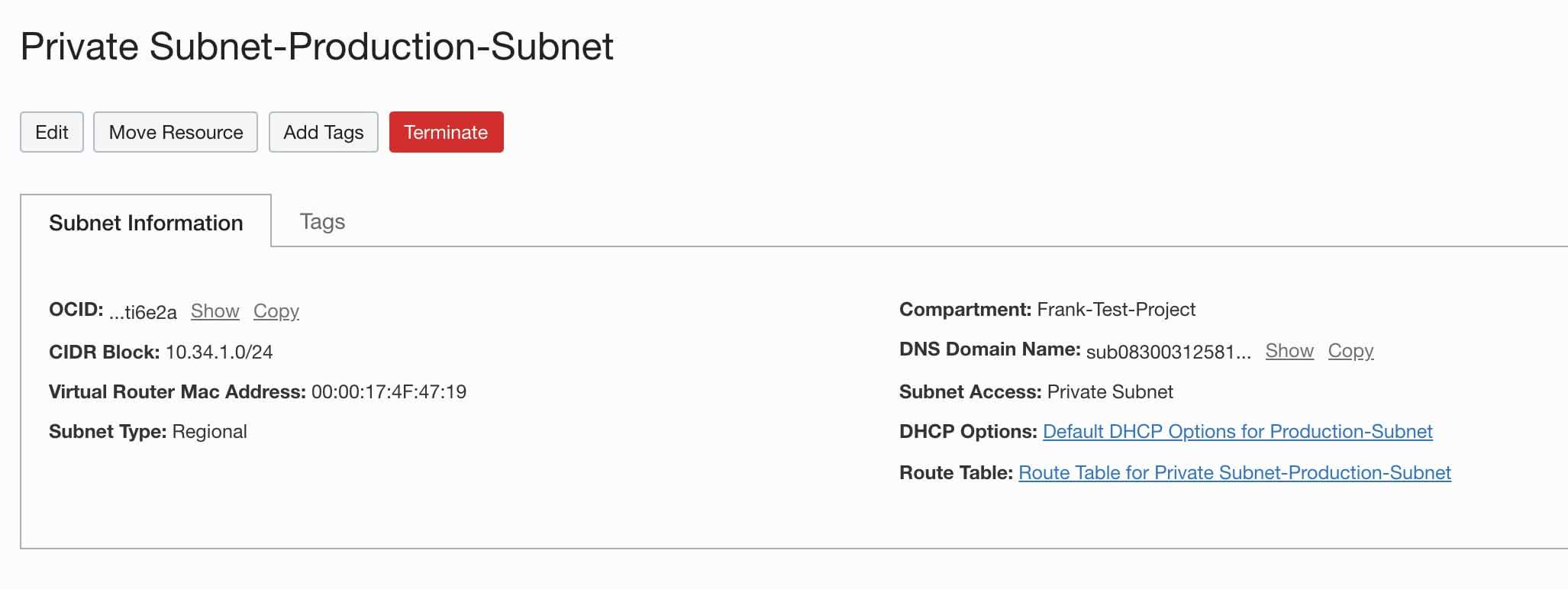
You should expect to see a NAT Gateway route rule.
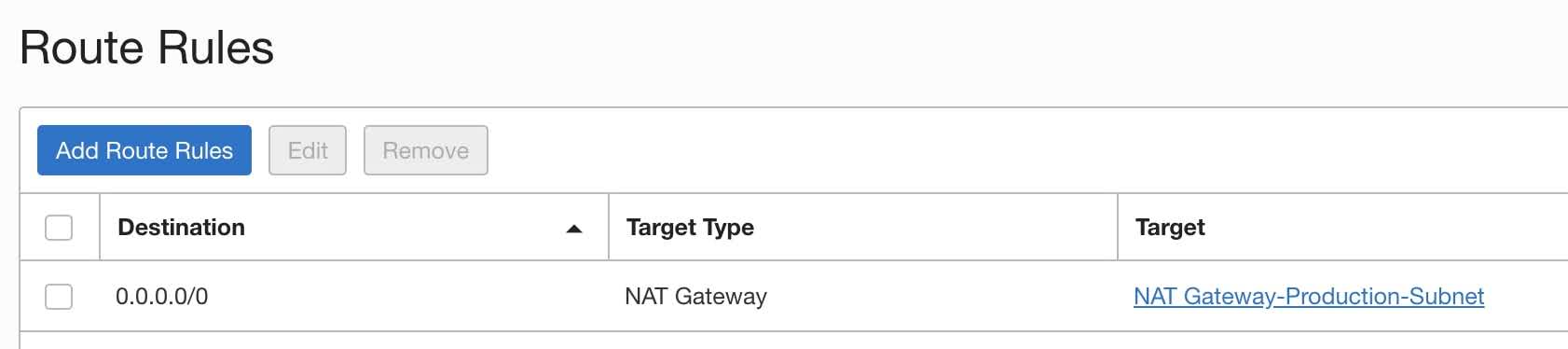
If you don’t have the above route rule then please create a NAT gateway and add the route rule to your subnet route table. You can find more details from here.
Create Network Security Group
Steps to create network security group
- Go to Networking > Virtual Cloud Networks page.
- Select your compartment under the List Scope section from the left bottom page.
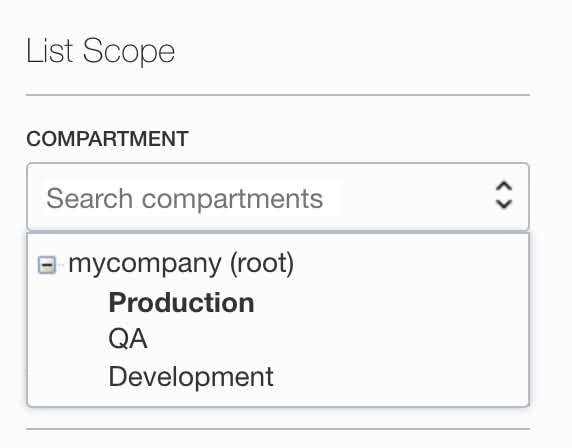
- Click your VCN.
- Click Network Security Groups under the Resources section from the left.
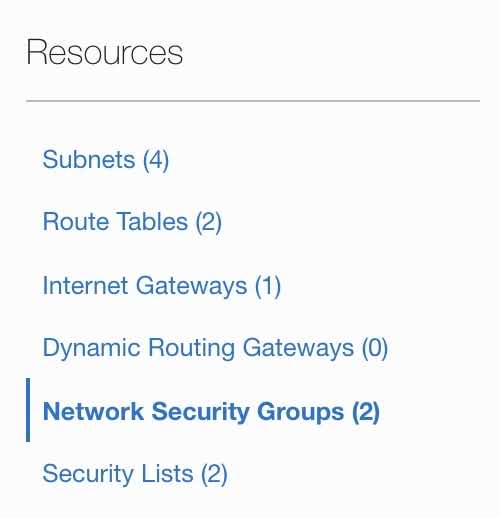
- Click the Create Network Security Group button and follow the instructions.
Step 5: Set Up Object Storage
This is an optional step and required only if you want to utilize PITR functionality.
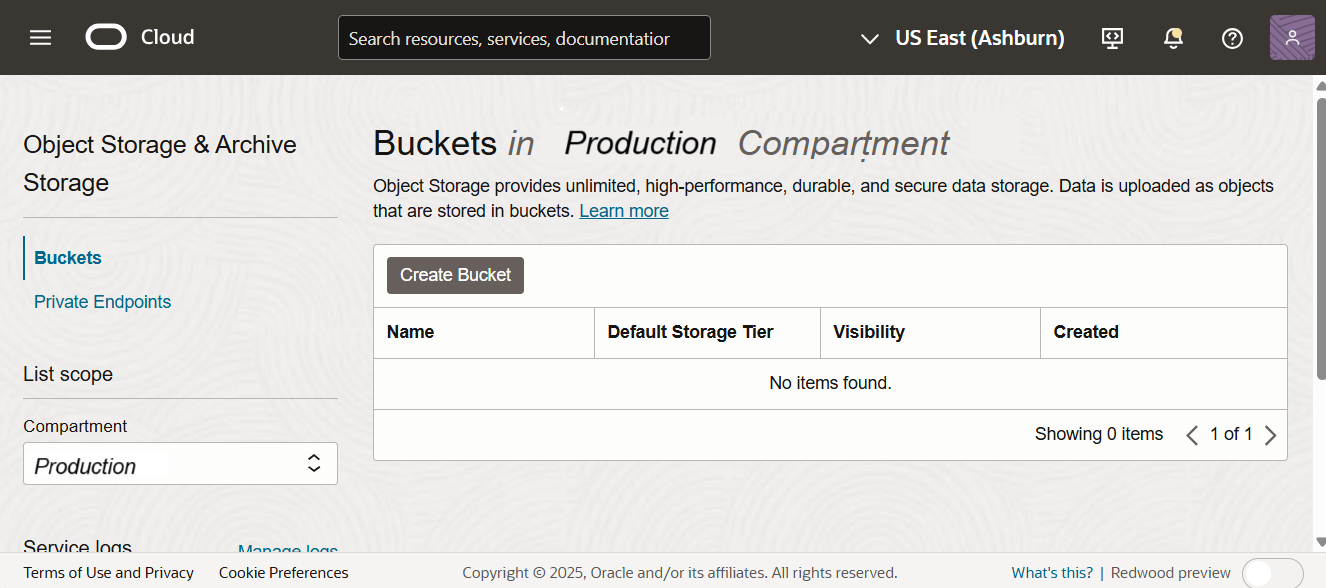
Create Object Storage Bucket
- Log in to the OCI console.
- Select your region.
- Go to Storage > Buckets under Object Storage & Archive Storage page.
- Select your compartment under the List Scope section on the bottom left page.
- Click Create Bucket.
-
Fill in the Bucket Name.
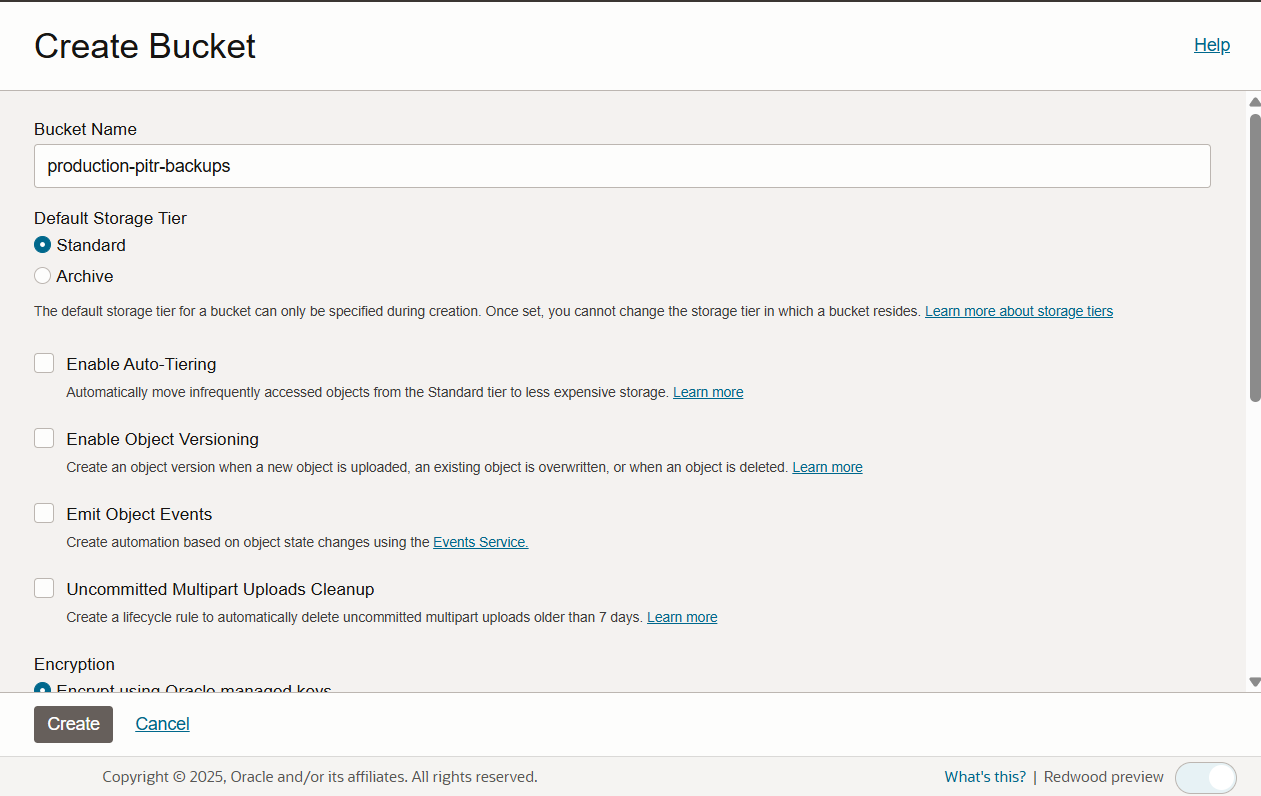
-
Click the Create button.
Note down the Namespace
-
Go to Storage > Buckets under Object Storage & Archive Storage page.
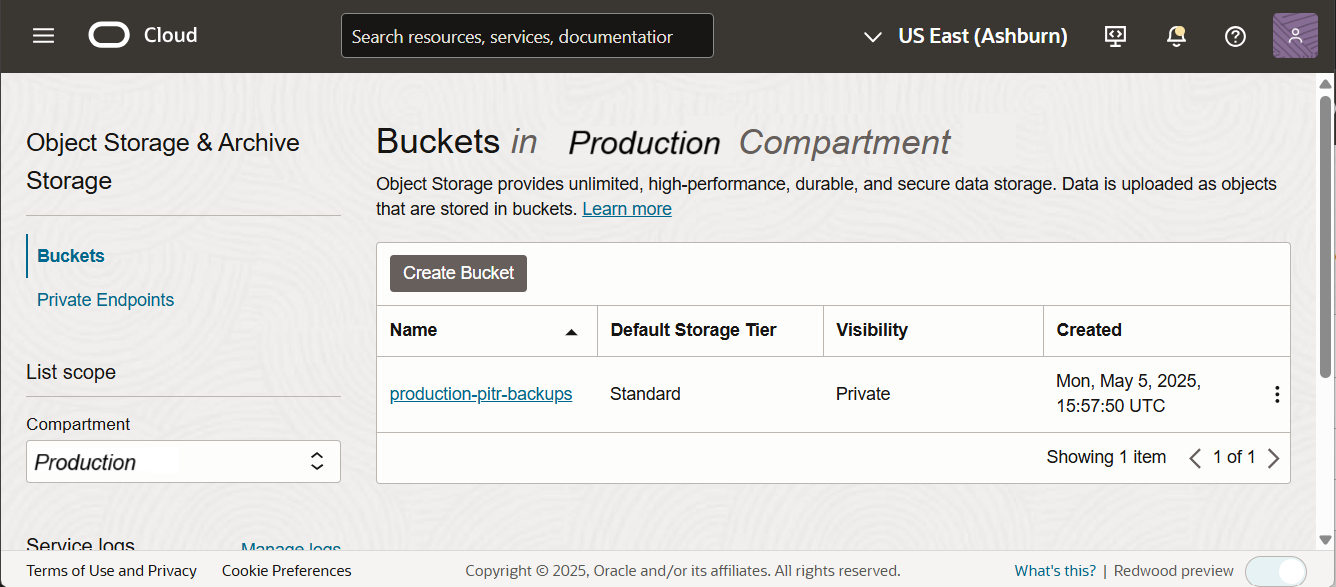
-
Click on the bucket you just created to open the Bucket Details page.
-
Namespace will be visible in the Bucket Details page.
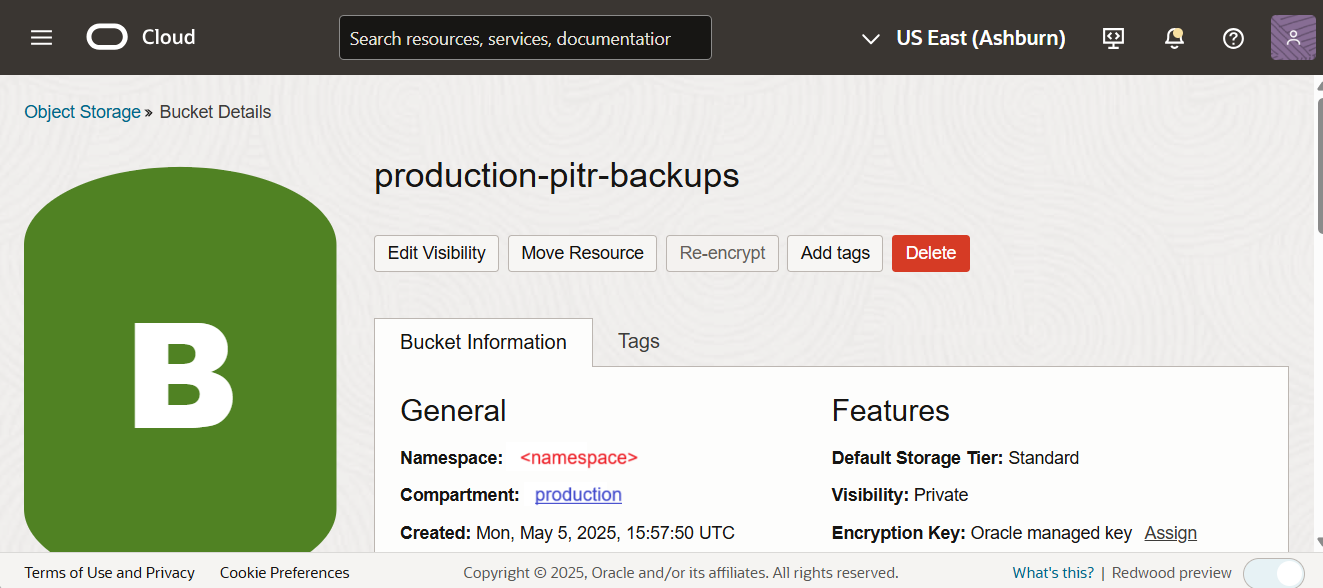
Create Customer Secret Keys
-
Login to OCI Console.
-
Select your Home Region.
-
Go to Identity & Security > Users page.
-
You can select the existing user or create a new one using Create User button.
-
Click Customer secret keys under the Resources section on the bottom left of the page.
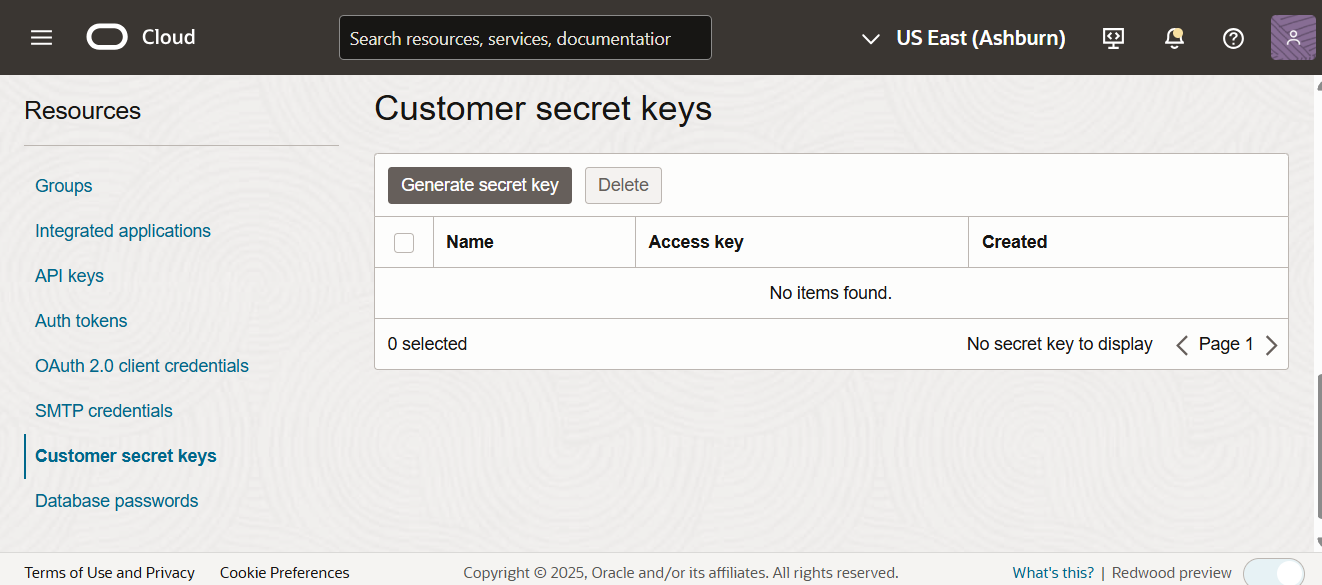
-
Click the Generate secret key button.
-
Fill in the name and click Generate secret key button.
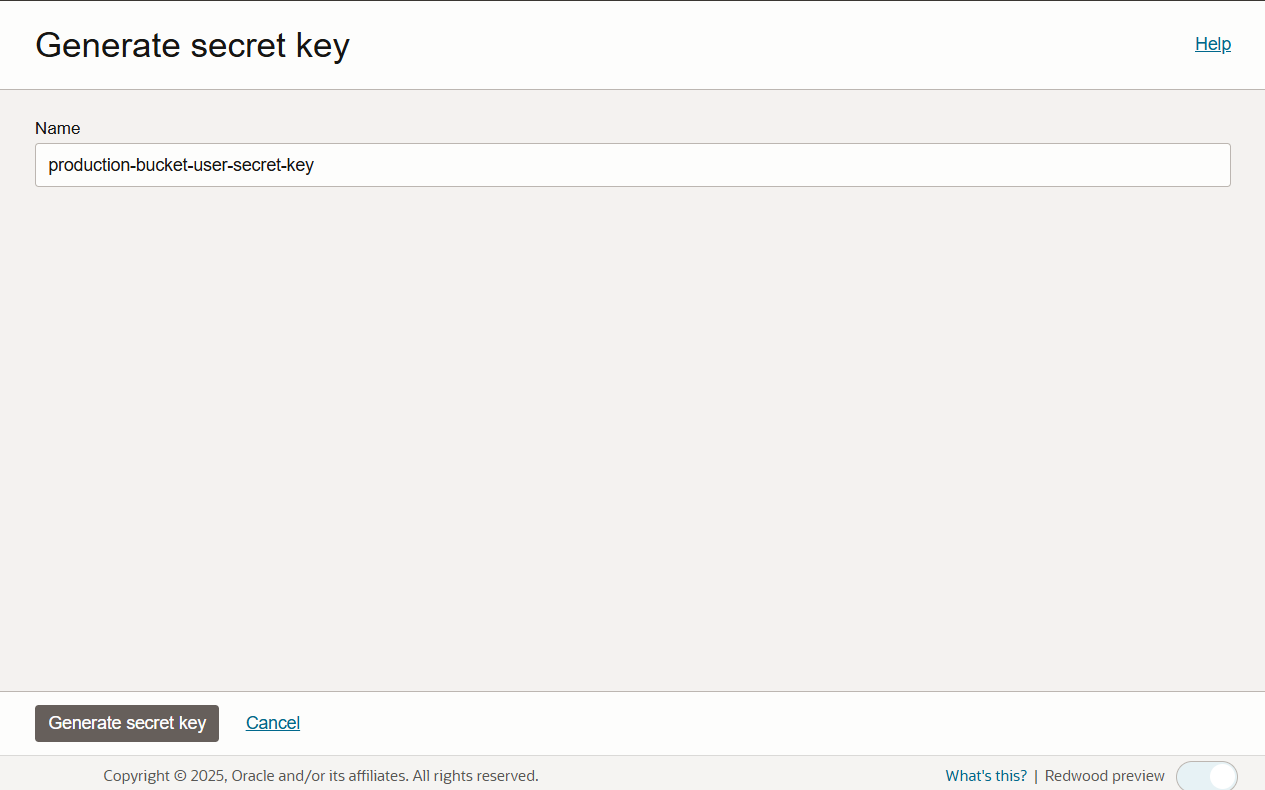
-
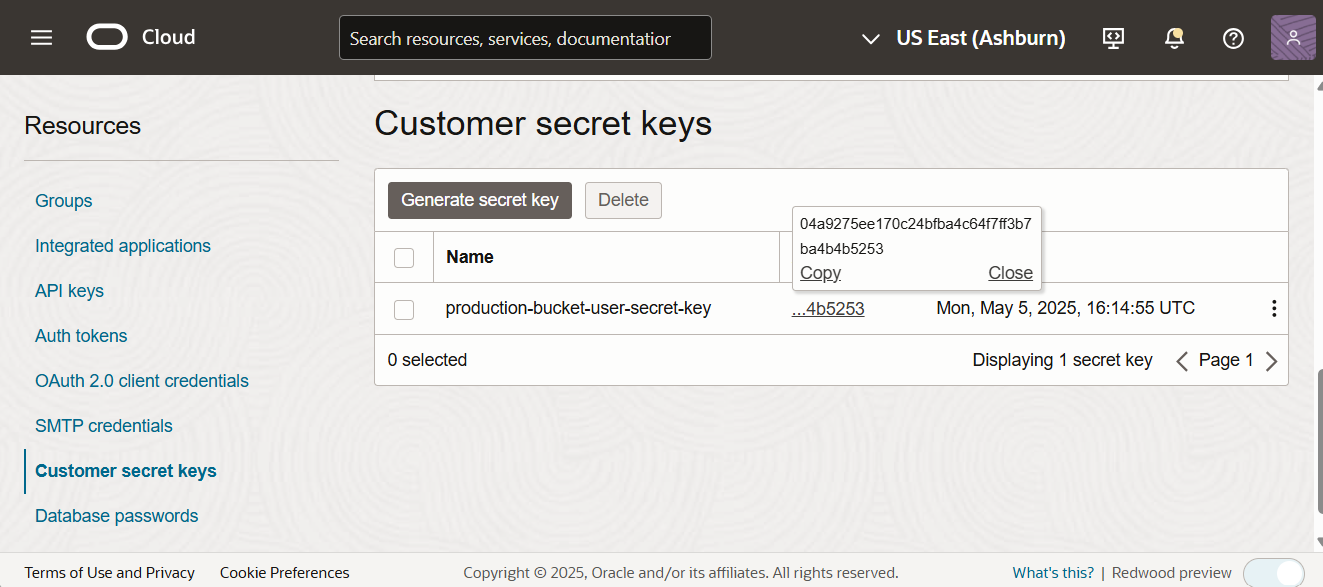
Copy the generated secret key and store it in a secure place.
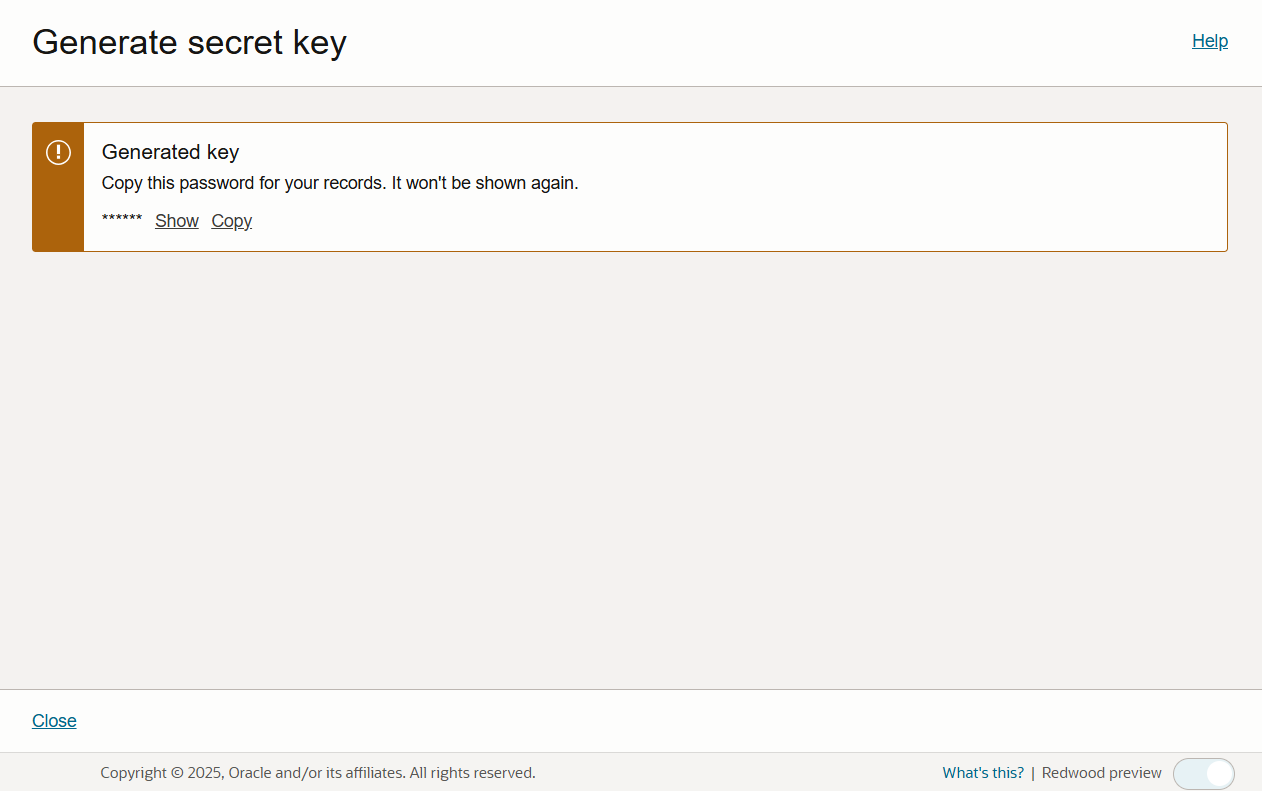
-
To copy the access key, go to the customer secret keys under the Resource section.
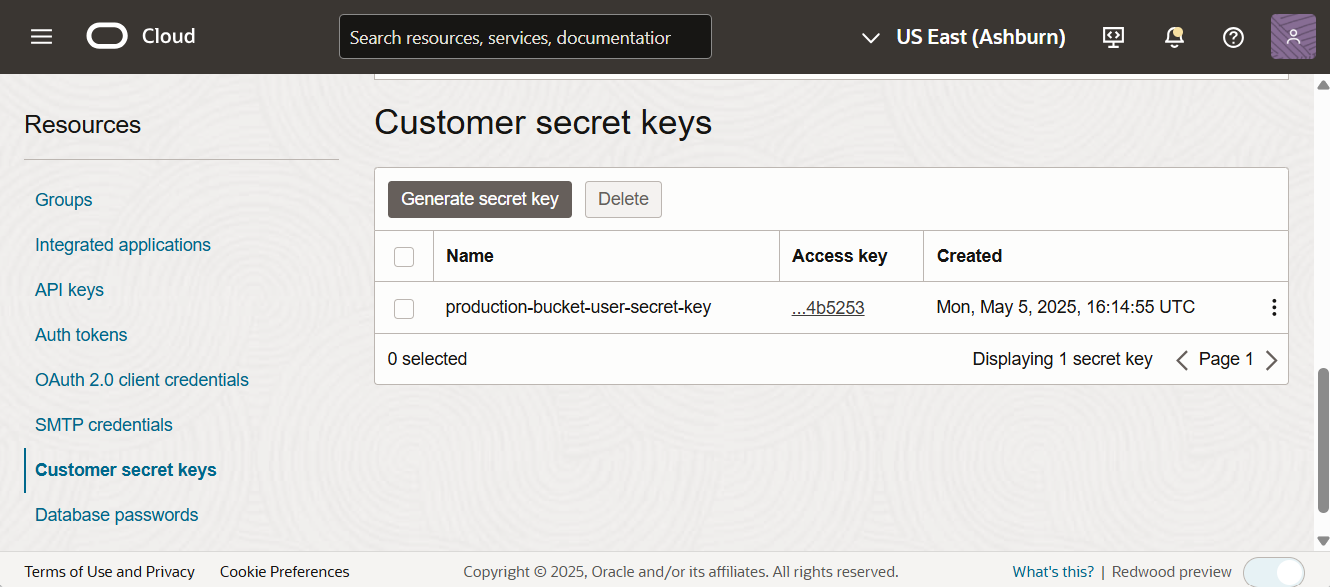
-
Hover on the Access key and it will show a popup and click on Copy button.
Add/Update Policy for the User to use Object Storage bucket
-
Login to OCI Console.
-
Select your Home Region.

-
Go to Identity & Security > Policies page.

-
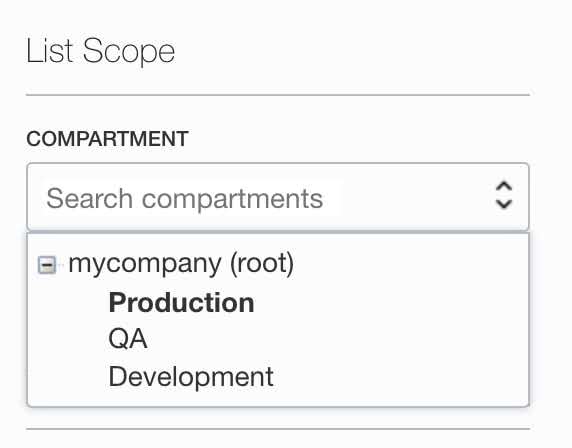
Select your compartment under the List Scope section on the bottom left page.
-
Create a new policy or update existing policy with below policy statements:
Allow group<Group name>to read buckets in compartment<Compartment name>
Allow group<Group name>to manage objects in compartment<Compartment name>where all{target.bucket.name='<Bucket name>', any \{request.permission='OBJECT\_CREATE', request.permission='OBJECT\_INSPECT', request.permission='OBJECT\_DELETE', request.permission='OBJECT\_READ'}}
Now you have all the details required for the Object Storage configuration
Namespace
Access Key
Secret Key
Region
Bucket name
Required OCI information for creating ScaleGrid Cloud Profile
You need to provide the following information to create a ScaleGrid Cloud Profile.
- Region - A subscribed region in OCI where you wanted to deploy your database cluster.
- Tenancy OCID - Tenancy Oracle Cloud Identifier (OCID) is an Oracle-assigned unique ID of your tenancy.
- User OCID - User OCID is a unique ID of the user that you have created in the previous step.
- User API Fingerprint - See Add user API key section for more information.
- Compartment OCID - The compartment where your database cluster will be hosted. The compartment OCID can be found in Identity > Compartments > Compartment Details page.
- User API Private Key - The private key that you have created in the Add user API key section.
- VCN, Subnet and Network Security Group - You should have created at least one VCN with a Subnet and Network Security Group in your compartment for database clusters.
- Compartment Tag Namespace - If you're using a speciifc compartment instead of the root tenancy for the ScaleGrid Tag Namespace.
* Redis is a trademark of Redis Labs Ltd. Any rights therein are reserved to Redis Labs Ltd. Any use by ScaleGrid is for referential purposes only and does not indicate any sponsorship, endorsement or affiliation between Redis and ScaleGrid.
Updated 9 months ago
